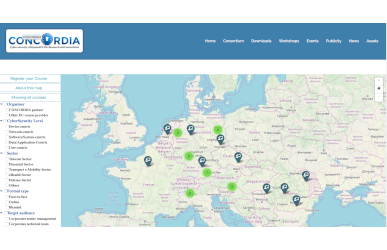
Assets
Here are presented CONCORDIA’s assets:
Delivered Outcomes
We structured our 20 outcomes into five categories – Policy, Tools, Education, Pilots, and Certification. The sixth category is focused on Research and contains 28 selected publications. Find more here!

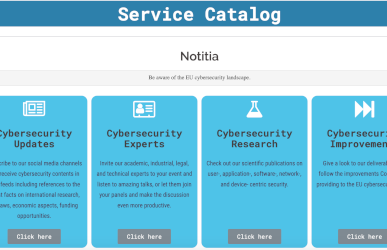
CONCORDIA Service Catalog:
Education for Professionals
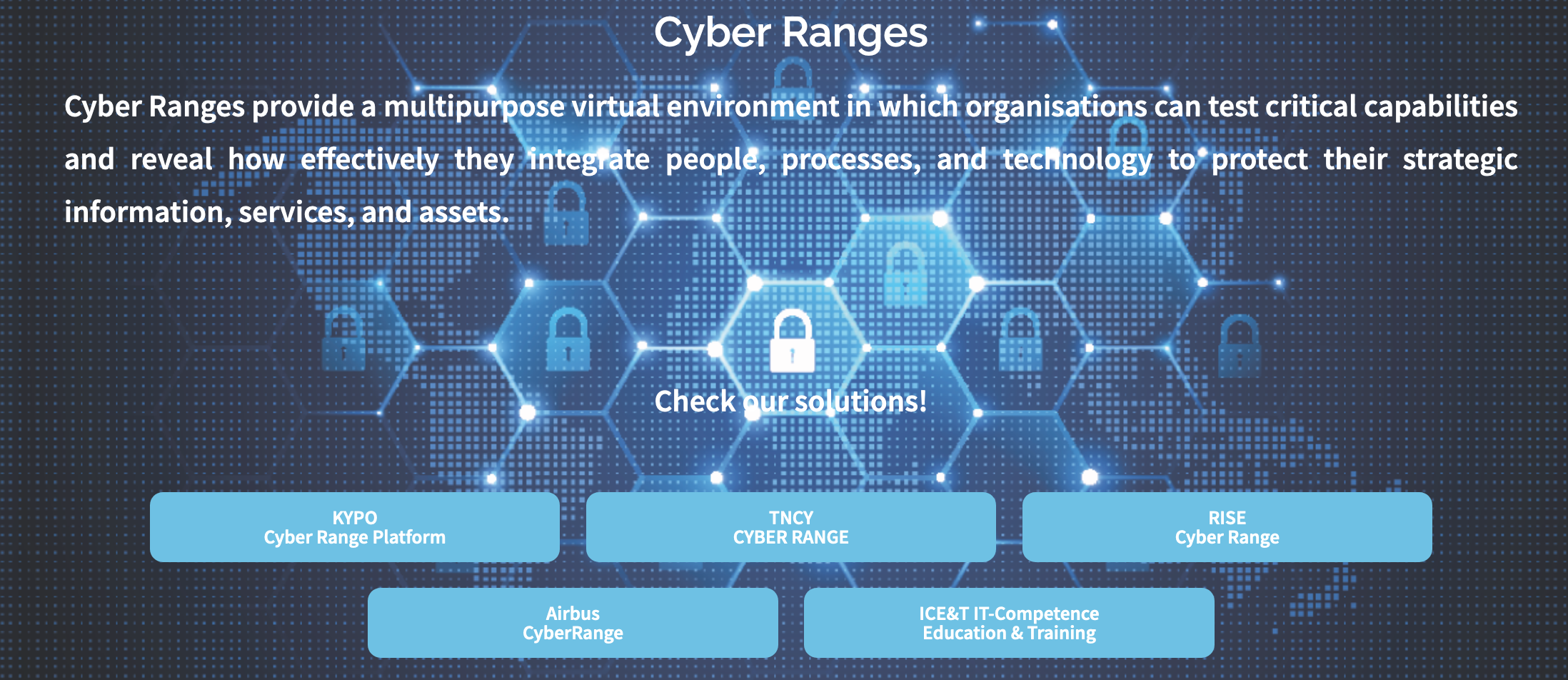
Cyber Ranges
Labs
Economic Aspects of Cybersecurity
Legal Aspects of Cybersecurity
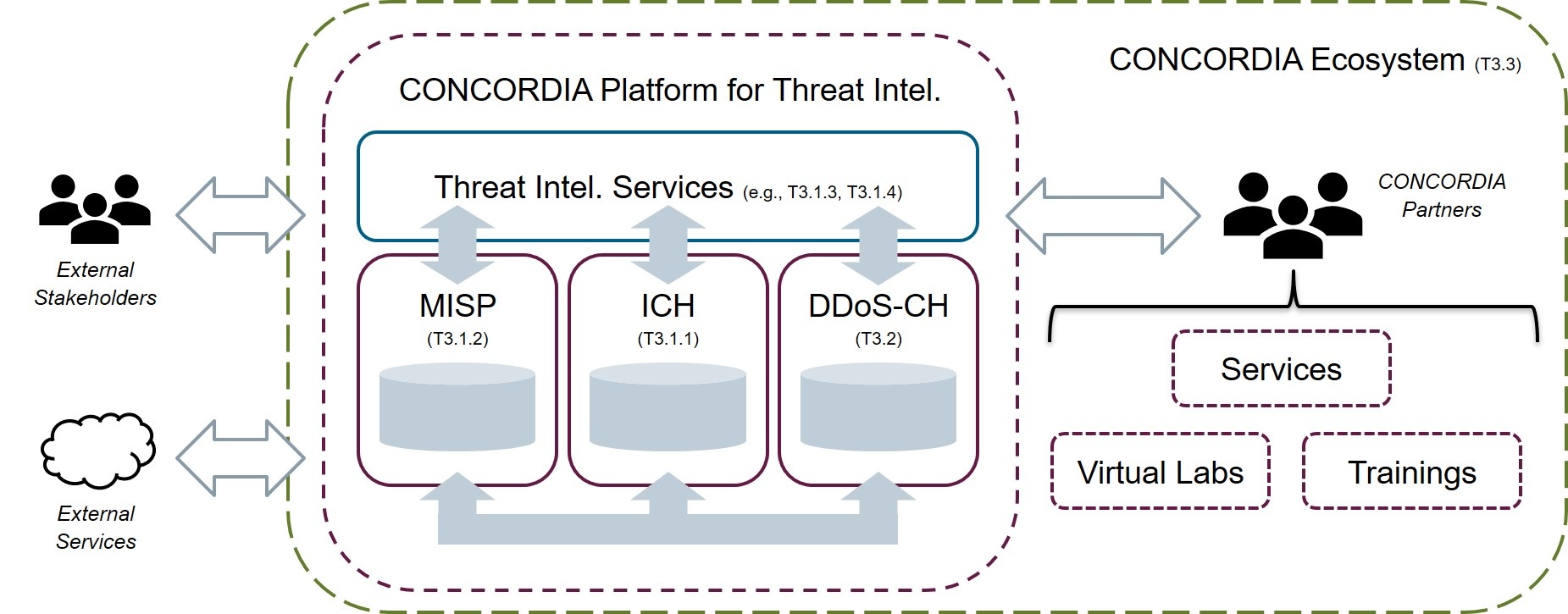
Threat Intelligence Platform
Cybersecurity Roadmap for Europe
CONCORDIA Service Catalog for Cybersecurity Experts, Start-ups, SMEs, Industry, Community
Towards a European Education Ecosystem for Cybersecurity