Work in Progress: the CONCORDIA Platform for Threat Intelligence
Our first steps to improve Europe’s information position in cybersecurity
We present CONCORDIA’s vision for a cross-sector, pan-European platform for collecting, analyzing, and sharing threat intelligence, which combines datasets built up in different parts of the project.
What is threat intelligence?
Threat intelligence can be defined as the process of acquiring knowledge from multiple sources about threats to an environment. Threat intelligence supports informed decision-making on cybersecurity by providing information about attack techniques, indicators of compromises, and vulnerabilities. The process is essentially collaborative and based on real-world datasets.
CONCORDIA’s approach
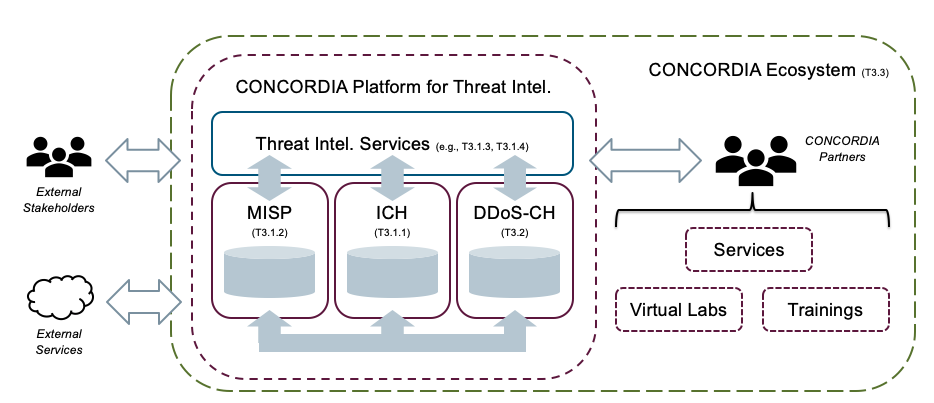
The two cross-sector pilots in CONCORDIA (“Building a Threat Intelligence for Europe” and “Piloting a DDoS Clearing House for Europe”) are developing the basic building blocks for a pan-European and cross-sector threat intelligence platform, which conceptually forms a central point of contact for all services within the CONCORDIA ecosystem that are related to threat intelligence.
We are developing the CONCORDIA threat intelligence platform based on three primary principles:
- Multi-source: the platform uses multiple datasets available through heterogeneous technologies and providing different data management services (e.g., two clearing houses and their specific services).
- Combine datasets: the platform uses algorithms to integrate datasets into new derived datasets (e.g., coupling reported botnet infections and DDoS attacks, see the scenario below).
- Uniform engagements rules: applications access (derived) threat intel data and usage policies through a common and well-defined threat intelligence interface.
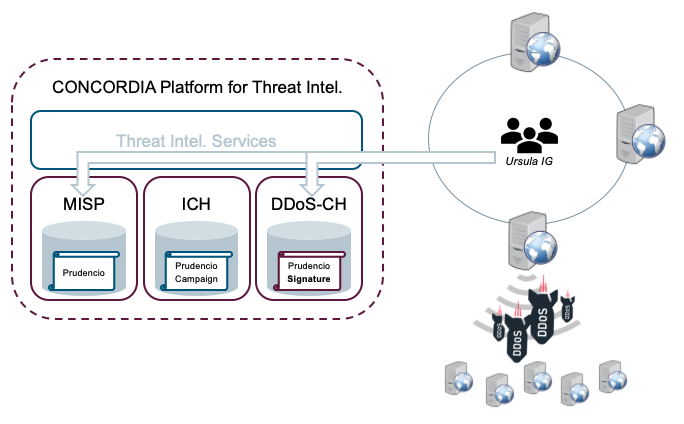
Figure 1 shows the resulting platform architecture, which consists of three core components:
| MISP | The central instance, which is the main gateway for TI information on the CONCORDIA platform. It concentrates information from malware, vulnerabilities, target attacks and more. |
| ICH | The Incident Clearing House (ICH), which collects information about vulnerable and compromised systems and forwards that information to the resource owners. |
| DDoS-CH | The DDoS Clearing House (DDoS-CH) which contains descriptions of the characteristic of DDoS attacks (e.g., source addresses and average packets per second) in the form of so-called “DDoS fingerprints”. |
The other key component of the platform is a layer of threat intel services, which contains algorithms that combine datasets from the core components and make the result available to users (e.g., CONCORDIA services and partners) through a well-defined threat intel interface.
A use case description
The following scenario (with hypothetical players and incidents) illustrates how the CONCORDIA threat intel platform can support the fight against an emergent DDoS booter service.
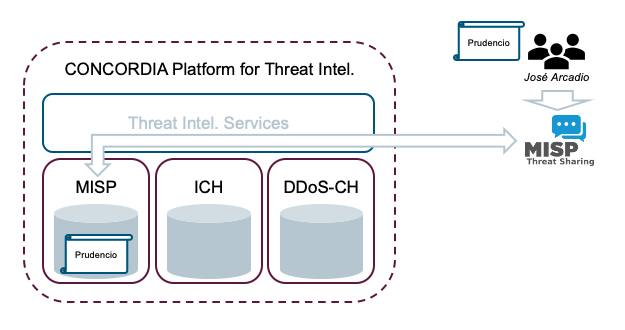
In the context of a cybersecurity improvement program, a team from the company José Arcadio (a company participating in the CONCORDIA Ecosystem) starts gathering information about a new booter service sold on the dark web. They push all collected information to their local MISP instance and synchronise with the central CONCORDIA MISP instance (see Figure 2). The information includes a report on a new booter service called “Prudencio”, which is known to carry out DDoS attacks on financial institutions.
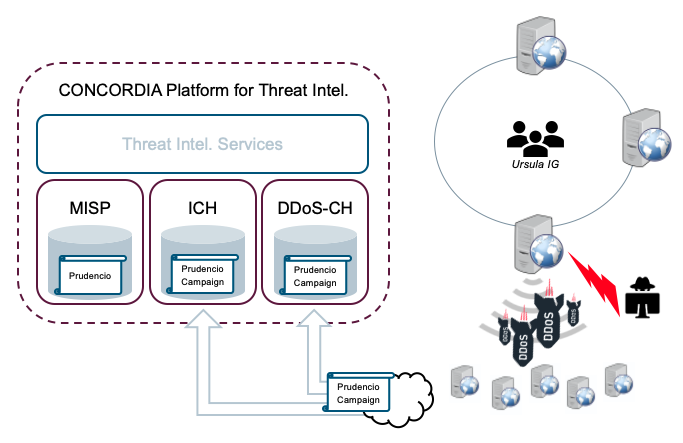
Meanwhile, the ICH starts receiving notifications of systems compromised by the Prudencio botnet. Among the notifications, one forensics investigator reveals that a specific compromised server is linked to an IP address belonging to another company within the CONCORDIA ecosystem, the investor group “Ursula IG”.
Immediately after receiving the notification, the ICH automatically warns Ursula IG’s security team and references any useful information currently available in the central CONCORDIA MISP instance. The DDoS-CH observes denial-of-service attacks that Prudencio launches and begins collecting fingerprints that can be used to detect and subsequently neutralise the DDoS attacks (Figure 3).
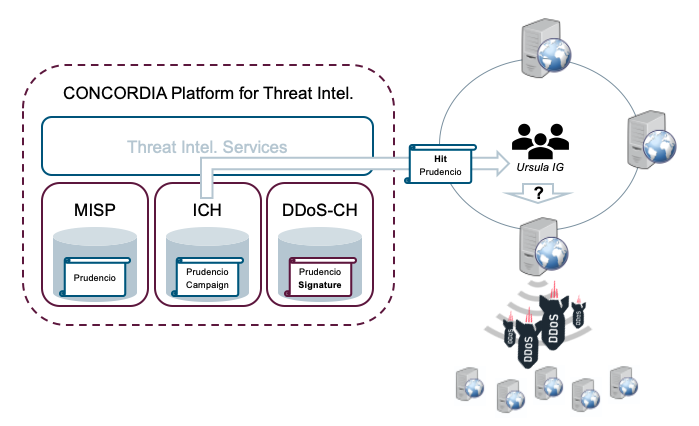
After receiving the notification from the ICH, the security team at Ursula IG verifies the problem and confirms the incident: one of their web servers has been compromised. At this point, the team checks all available threat intelligence accessible on the central CONCORDIA MISP instance and starts organising incident response.
In the meantime, the team has already received a further notification from the DDoS-CH, signaling the availability of detection signatures for Prudencio-related DDoS attacks. The incorporation of those signatures (Figure 4) within the previously deployed security tool chains (e.g. intrusion prevention and detection systems) allows Ursula IG to protect its other web servers while the compromised server is cleaned.
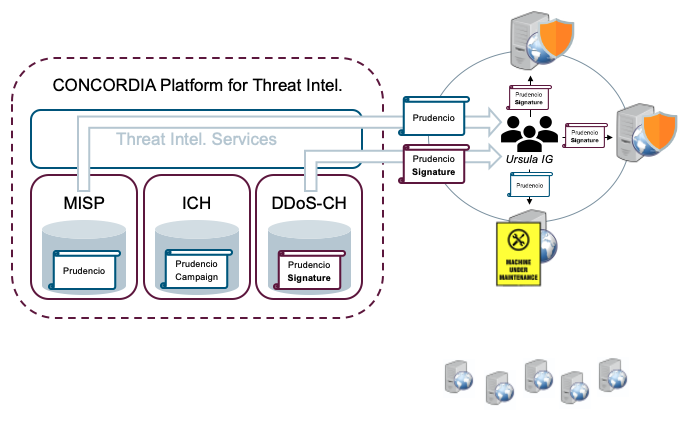
and Ursula IG applying mitigation and cleanup actions (bottom).
Next steps
After defining the platform design, we will be working on the definition of the available resources (catalogs) in each of the core components (the databases). These catalogs are the first step to build a common interface that will combine data from multiple sources. Once we have this interface in place, additional components will be developed to share and to correlate threat intelligence information.
(By Marco Caselli (Siemens AG), João Ceron (SIDN Labs), Christian Keil (DFN-CERT), Jan Kohlrausch (DFN-CERT), Cristian Hesselman (SIDN Labs))
