A new method to detect exploitable smart-home devices connected behind a NAT
Instead of relying on customers to protect their vulnerable smart home devices from being used in cyberattacks, Ben-Gurion University of the Negev (BGU) researchers who participate in CONCORDIA have developed a new method that enables telecommunications and internet service providers to monitor these devices.
According to their new study, the ability to launch massive distributed denial-of-service (DDoS) attacks via a botnet of compromised devices is an exponentially growing risk in the Internet of Things (IoT). Such massive attacks, possibly emerging from IoT devices in home networks, impact the attack target, as well as the infrastructure of telecommunication service providers (telcos). This real-world problem has already caused challenging attacks in Germany and Singapore, and poses a risk to telco infrastructure and their customers worldwide.
Each connected device has a unique IP address. However, home networks typically use gateway routers with NAT (network address translation) functionality, which replaces the local source IP address of each outbound data packet with the household router’s public IP address. Consequently, detecting connected IoT devices from outside the home network is a challenging task.
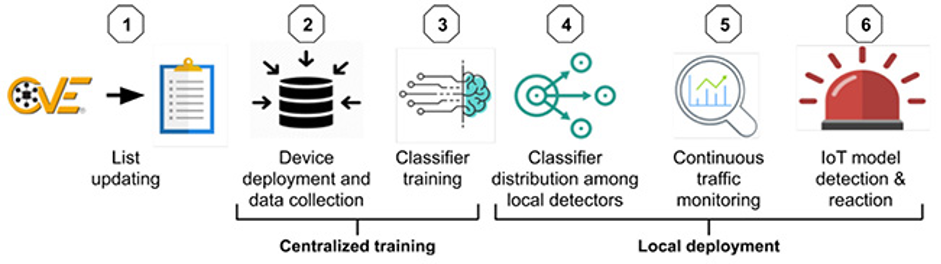
The researchers developed a method to detect connected, vulnerable IoT models before they are compromised by monitoring the data traffic from each smart home device. This enables telcos to verify whether specific IoT models, known to be vulnerable to exploitation by malware for cyberattacks are connected to the home network. It helps telcos identify potential threats to their networks and take preventive actions quickly. In the case of a potential DDoS attack, this method would enable the telco to take steps to spare the company and its customers harm in advance, such as offloading the large volume of traffic generated by an abundance of infected domestic IoT devices. In turn, this could prevent the combined traffic surge from hitting the telco’s infrastructure, reduce the likelihood of service disruption, and ensure continued service availability.
The full (open access) research paper can be found here: https://doi.org/10.1016/j.cose.2020.101968
The (open access) associated dataset can be found here: https://zenodo.org/record/3924770. Further details about BGU’s IoT Security Research Lab can be found here: https://cyber.bgu.ac.il/iot-security/
This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 830927.
(By Yair Meidan and Prof. Asaf Shabtai, Ben-Gurion University of the Negev (BGU).)
