Assessing blockchains’ network infrastructure: why it matters for cybersecurity
Blockchain got a tremendous attention in the last few years and is considered as a disruptive technology able to redefine the collaborative processes in many activity domains including the cybersecurity. The billions of assets exchanged on a daily basis by public blockchains make them a new and attractive target for attackers so that blockchains can be considered in a dual way regarding cybersecurity: both as a target to protect as well as a new tool to build new collaborative defense mechanisms. For instance, solutions have been proposed to create a blockchain-based platform to help detect and fight against distributed denial of service[1], or provide a secure logging of security incidents, but many other applications are possible in the field of cybersecurity. A part of our scientific job in CONCORDIA will be to assess blockchains’ network infrastructure so that they can be used to implement the future tools developed by the project to enhance Europe’s digital sovereignty.
With the raise of such collaborative platforms, the question of the performance and the resiliency of the blockchain networking infrastructure arises. Indeed, the P2P infrastructures and protocols supporting the blockchains become critical assets as more and more money and services are made on top of them. However, they are largely undocumented and may be prone to severe attacks. With regard to the state of the art on P2P networks security, the fact that a service infrastructure is distributed is not sufficient to assess its reliability, as many bias (for instance, if nodes are concentrated in a given geographical location) and attacks (eclipse attack, Sybil attack or partition attack) are still possible and may severely disturb the network. So, before further developing new security services on top of blockchains, it is of prime importance to analyze the underlying network to unveil possible limitations and vulnerabilities.
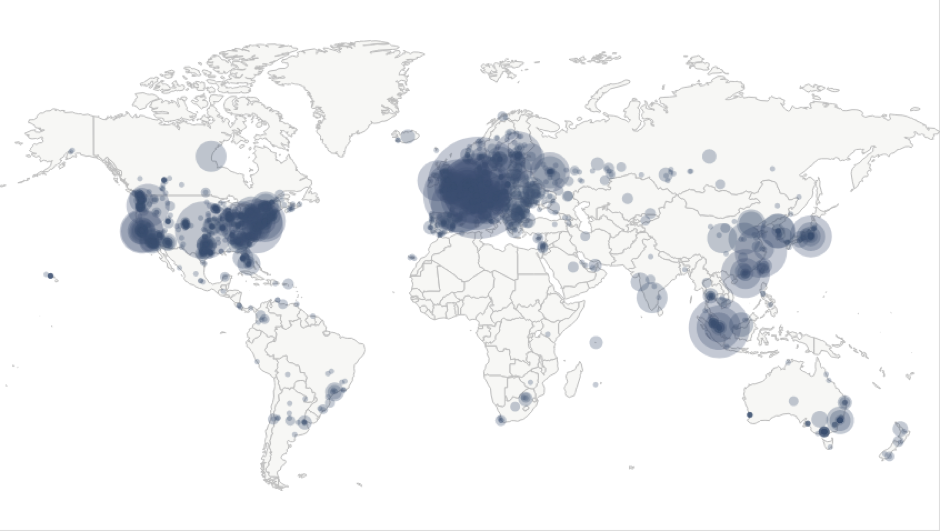
Overall, according to the scientific literature, the security provided by the proof of work consensus and the huge size of the main public blockchains seem to protect them well from large scale attacks (51% attack, selfish mining attack, etc.) whose cost to be successful becomes prohibitive and often exceeds the expected gain. However, rather than only focusing on the application level, an attacker could rather try to disturb the underlying P2P network to weaken the consensus in some specific parts of the blockchain network to gain advantage. For instance some studies[2] show that an adversary can hijack Internet routing to delay the propagation of blocks. At the blockchain’s network level, previous versions of both Bitcoin[3] and Ethereum[4] main clients had flaws facilitating the isolation of nodes by an attacker (for instance, by monopolizing all of its outgoing and incoming connections), but they have been corrected since then and are efficient to mitigate large attacks. The question we will try to answer in the following months is to know if, being given real blockchains’ network topologies instantiated in an emulated environment, small attacks targeting a few number of nodes could still provide attackers a significant advantage over the blockchains or not?
(By Thibault Cholez, Jean-Philippe Eisenbarth, Olivier Perrin. University of Lorraine)
References
- B. Rodrigues, T. Bocek, A. Lareida, D. Hausheer, S. R. Niya, and B. Stiller. A blockchain- based architecture for collaborative DDoS mitigation with smart contracts. In 11th IFIP Inter- national Conference on Autonomous Infrastructure, Management and Security (AIMS 2017), pages 16–29. Springer, Heidelberg, July 2017.
- M. Apostolaki, A. Zohar, and L. Vanbever. Hijacking Bitcoin: Routing Attacks on Cryptocur-rencies. In 2017 IEEE Symposium on Security and Privacy (SP), pages 375–392, San Jose, CA, USA, May 2017. IEEE.
- E. Heilman, A. Kendler, A. Zohar, and S. Goldberg. Eclipse attacks on bitcoin’s peer-to-peer network. In Proceedings of the 24th USENIX Conference on Security Symposium, SEC’15, pages 129–144, Berkeley, CA, USA, 2015. USENIX Association.
- Y. Marcus, E. Heilman, and S. Goldberg. Low-resource eclipse attacks on Ethereum’s peer-to-peer network. IACR Cryptology ePrint Archive, 2018:236, 2018.
