Cyber-attack impacts on multi-UAV missions: key observations to guide mission design
Many applications can benefit from the use of groups of collaborating unoccupied aerial vehicles (UAVs), including logistics, disaster management, or fire monitoring and prevention. However, like all other computing and communicating platforms, UAVs can be vulnerable to cyber-attacks, which may jeopardise their mission, fully or partially.
As part of CONCORDIA, our team, consisting of researchers from Imperial College London and Airbus Defence and Space, has investigated how to analyse the impact of attacks on the viability of multi-UAV missions, and how to design missions resilient to attacks. Here, we outline some of the methodology followed and our key observations, focussing on a scenario of multi-UAV fire survey missions.
Key considerations: attack progression, containment and recovery
To estimate the impact of an attack on a group of UAVs, we have built a model for estimating mission performance over time given a possible attack scenario. We intend our model to be used as a tool to aid mission planning, and to decide whether to continue a mission when a cyber-attack has occurred. Although reasoning about the impact of failures is common, cyber-attacks differ significantly from failures, for example because they can propagate from vehicle to vehicle. Consequently, estimating attack impact must also account for attack propagation, and we model the stages of attack spread between UAVs, based on the vehicle connectivity topology. This enables us to assess the likely outcomes of different attack scenarios, for example, with different propagation speeds or attack containment countermeasures.
UAV missions are typically of short duration, as the flight time is limited by the battery capacity. Repair is therefore typically not an appropriate resiliency measure, and replacement vehicles are more likely to be used to ensure mission viability. Our analysis shows that such additional resourcing can help recover mission capacity. However, whether the recovery is sufficiently effective also depends on how rapidly the attack can spread and requires models such as the ones we have built.
Limiting the propagation of the attack (i.e., containment) is also possible by severing communication links or removing compromised UAVs from the mission. If this can be done fast enough, and early enough, the impact of the attack can be significantly reduced and the need for recovery capacity is lower.
Main takeaway: Use a model to quantify impact
So, different solutions can be adopted, with different consequences. Although these may seem intuitive, quantifying their impact requires detailed modelling and analysis. For example, when an attack is competing against its containment the outcome is difficult to predict through intuition alone: How many vehicles will need to be isolated? Will those remaining be enough to complete the mission? What recovery capacity will be enough to complete the mission to an acceptable standard?
The model and the approach we have developed enables quantifying these aspects and determining how different approaches to cyber-attack resilience can be used in alternation or in combination, to determine to what extent the mission’s objectives can be achieved, what recovery capacity is necessary to ensure mission viability, or whether the mission is best abandoned.
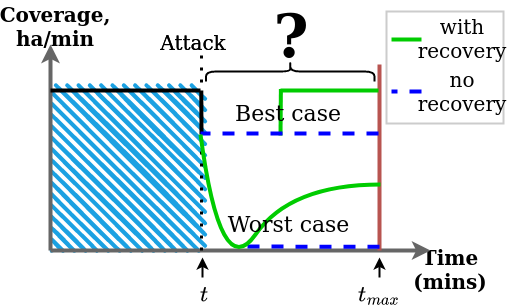
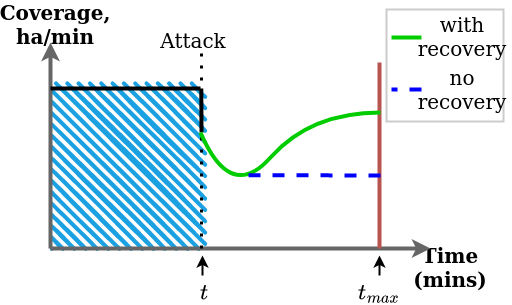
This approach is shown in the figures below, which depict the area coverage reached by a fire-survey mission, where a cyber-attack occurs at time t. Figure 1 highlights the problem when no model is used – the outcome from the interplay between the attack, defence and recovery is broadly unknown. Our approach, shown in Figure 2, allows us to build a quantified expectation of what is likely to happen, based on the different parameters, and to make decisions at the planning stage or during the mission itself.
Conclusion
Cyber-resilience of collaborative missions is a challenging research problem and decisions cannot be made on intuition alone. Models are required to understand how attacks unfold, and to quantify their impact on the system functionality. Our first article on doing this for multi-UAV missions is listed below. More to follow. Stay tuned!
[1] J. Soikkeli, C. Perner and E. C. Lupu, “Analyzing the Viability of UAV Missions Facing Cyber Attacks,” 2021 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), 2021, pp. 103-112, doi: 10.1109/EuroSPW54576.2021.00018.
(By Jukka Soikkeli and Emil Lupu, Imperial College London)
