Cybersecurity threats: trends
Driven by digitalization, information sharing has been experiencing an exponential growth in the past few years. In turn, one’s eagerness to better prepare and protect depends on the ability to change the attitude from “need to know” to “need to share”. Digital technologies, most notably Artificial Intelligence (AI), have shaped decision-making, everyday communication, life and work, hence highlighting the importance of maintaining the online economy and ensuring its prosperity.
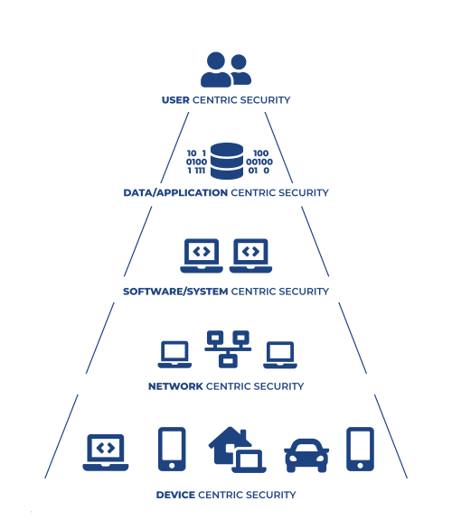
Threat landscape is continuously changing and evolving to address the evolution of the IT environment from software to IoT, via services and cloud computing. Providing an up-to-date overview of the current state of the art on threats and cybersecurity is critical to provide a picture of the status of cybersecurity and evaluate new trends in cybersecurity focusing on emerging threats and evolving attacks. CONCORDIA cyber security threat analysis is inspired by the different research domains (Figure 1) and considers the following domains: (i) network-centric, (ii) system/software-centric, (iii) application/data-centric, (iv) user-centric, v) device centric security.
Network-centric security refers to the transportation of data as well as to the networking and the security issues associated with it. Topics range from DDoS protection, Software-Defined Networking (SDN), ad hoc networks to encrypted traffic analysis, 5G. System-centric security centers around cloud and virtualized environments, while IoT/Device-centric security centers around modern systems such as Internet of Things (IoT)/edge and corresponding devices, both targeting topics such as middleware, secure OS, and security by design, Malware analysis, systems security validation, detection of zero-days, and recognizing service dependencies are specifically addressed. Data-centric security addresses issues concerned with management, analysis, protection, and visualization of data at all layers of a given system/environment, focusing on modern Big Data environments. Application-centric security addresses issues related to the security of applications, like modern services and their management. User-centric security addresses issues like privacy, social networks, fake news and identity management. The above domains apply to any environments ranging from traditional distributed IT systems, to devices that produce raw data, such as embedded systems, sensors, IoT devices, drones, and the associated security-centric issues, such as IoT security, via service-based systems, such as, service-oriented architecture, cloud, microservices.
This analysis, which will be soon presented in the public deliverable D4.1, results in a comprehensive cybersecurity threat map (Table 1) that summarizes the mapping between generic threat groups and specific threats in the domain of interest. To this aim, threat group and threat identification have been inspired by the ENISA threat taxonomy.[1]
| Domain (D) | Threat Group (TG) | Threats (T) |
|---|---|---|
| Device/IoT (1) | Unintentional damage / loss of information or IT assets (1) | Information leakage/sharing due to human errors (1) Inadequate design and planning or incorrect adaptation (2) |
| Interception and unauthorised acquisition (2) | Interception of information (1) Unauthorised acquisition of information (2) |
|
| Intentional Physical Damage (3) | Device modification (1) Extraction of private information (2) | |
| Nefarious Activity/Abuse (4) | Identity fraud (1) Denial of service (2) Malicious code/software/activity (3) Misuse of assurance tools (4) Failures of business process (5) Code Execution and Injection (unsecure APIs) (6) |
|
| Legal (5) | Violation of laws or regulations (1) | |
| Organisational threats (6) | Skill shortage (1) | |
| Network (2) | Unintentional damage / loss of information or IT assets (1) | Erroneous use or administration of devices and systems (1) |
| Interception and unauthorised acquisition (2) | Signaling Traffic Interception (1) Data Session hijacking (2) Traffic Eavesdropping (3) Traffic Redirection (4) |
|
| Nefarious Activity/Abuse (3) | Exploitation of software bug (1) Manipulation of hardware and firmware (2) Malicious code/software/activity (3) Remote activities (execution) (4) Malicious code – Signaling amplification attacks (5) |
|
| Organisational (Failure Malfunction) (4) | Failures of devices or systems (1) Supply chain (2) Software bug (3) |
|
| System (3) | Unintentional damage / loss of information or IT assets (1) | Information leakage/sharing due to human errors (1) Inadequate design and planning or incorrect adaptation (2) |
| Interception and unauthorised acquisition (2) | Interception of information (1) Unauthorised acquisition of information (data breach) (2) |
|
| Poisoning (3) | Configuration Poisoning (1) Business process Poisoning (2) |
|
| Nefarious Activity/Abuse (4) | Identity fraud (1) Denial of service (2) Malicious code / software / activity (3) Generation and use of rogue certificates (4) Misuse of assurance tools (5) Failures of business process (6) Code Execution and Injection (unsecure APIs) (7) |
|
| Legal (5) | Violation of laws or regulations (1) | |
| Organisational threats (6) | Skill shortage (1) Malicious Insider (2) |
|
| Data (4) | Unintentional damage / loss of information or IT assets (1) | Information leakage/sharing due to human errors (1) Inadequate design and planning or incorrect adaptation (2) |
| Interception and unauthorised acquisition (2) | Interception of information (1) Unauthorised acquisition of information (data breach) (2) |
|
| Poisoning (3) | Data Poisoning (1) Model Poisoning (2) |
|
| Nefarious Activity/Abuse (4) | Identity fraud (1) Denial of service (2) Malicious code / software / activity (3) Generation and use of rogue certificates (4) Misuse of assurance tools (5) Failures of business process (6) Code Execution and Injection (unsecure APIs) (7) |
|
| Legal (5) | Violation of laws or regulations (1) | |
| Organisational threats (6) | Skill shortage (1) Malicious Insider (2) |
|
| Application (5) | Unintentional damage (1) | Security Misconfiguration (1) |
| Interception and unauthorised acquisition (2) | Interception of information (1) Sensitive data exposure (2) |
|
| Nefarious Activity/Abuse (3) | Broken Authentication and Access Control (1) Denial of service (2) Code Execution and Injection (unsecure APIs) (3) Insufficient logging and monitoring (4) Untrusted composition (5) |
|
| Legal (4) | Violation of laws or regulations (1) | |
| Organisational threats (5) | Malicious Insider (2) | |
| User (6) | Human Errors (1) | Mishandling of physical assets (1) Misconfiguration of systems (2) Loss of CIA on data assets (3) Legal, reputational, and financial cost (4) |
| Privacy breaches (2) | Profiling and Discriminatory Practices (1) Illegal acquisition of information (2) |
|
| Cybercrime (3) | Organized criminal groups’ activity (1) State-sponsored organizations’ activity (2) Malicious Employees or Partners’ activity (3) |
|
| Media amplification effects (4) | Misinformation/Disinformation campaigns (1) Smearing campaigns/Market manipulation (2) Social responsibility/Ethics-related incidents (3) |
|
| Organisational threats (5) | Skill shortage/Undefined cybersecurity curricula (1) Business misalignment/Shift of priorities (2) |
From the table, it emerges that threats groups are quite horizontal to the different domains. Some differences still exist due to the peculiarities of each area. Also, threats in the area of data and users are cross domain due to the fact that often data represent the target of an attack, while users are often seen both as a target and as a threat agent.
Given this Table we ask CONCORDIA members to rate the relevance of the listed threats from 1 (low) to 5 (very high) using a questionnaire. From this first evaluation, it emerges that system threats (average score 3.78) are considered the ones entailing a higher risk, followed by application threats (average score 3.74) and device/IoT (average score 3.67), network (average score 3.59), and finally data (average score 3.48) and user (average score 3.35) threats. The user threats are considered the least risky, due to the composition of the CONCORDIA consortium, while data threats are often perceived as threats that impact all domains of interest and are therefore rated slightly lower than the same threats applied to a specific domain. The complexity of today IT systems is increasing the concerns about security, making system threats the most relevant. Applications with IoT/device threats are also considered very relevant, showing how current technology evolutions are changing the security perspective and perception.
To conclude, involvement of external stakeholders is important in activities of this type. We therefore prepared a similar questionnaire available at https://ec.europa.eu/eusurvey/runner/9eec529f-9a7d-197a-93c9-618617f22031, where you can rate the relevance of each threat in the table from 1 (very low relevance) to 5 (very high relevance) in their specific area(s) of business. Let you opinion count, join us in filling the questionnaire!
(By Marco Anisetti, Claudio Ardagna and Ernesto Damiani, UNIMI)