DNS Resolvers and DDoS: The Good, the Bad and the Ugly
DNS is one of the core components of the Internet infrastructure, but like any other service on the Internet, DNS is also misused in a set of Cyber attacks, from DNS cache poisoning, to DNS hijacking, to Reflection and Ampli fication (R&A) DDoS attacks. In a DNS-based R&A DDoS attack, DNS resolvers are misused both to hide the source of the attack and to make the attack much stronger. This is usually done by sending DNS queries with a spoofed source address to open DNS resolvers. These resolvers then respond to a victim who has not issued even a single one of those DNS queries. This together with some other security issues is why running an open DNS resolver is considered as a bad practice and in general (with the exception of public DNS servers) DNS servers are supposed to only serve the clients of the same network.
Many countermeasures have been thought of to stop or at least reduce the impact of the R&A DDoS attacks. For example at the origin side to prevent attackers from sending out spoofed packets, Source Address Validation (BCP38) was introduced and implemented. However, not all networks implement SAV, leaving the attackers with enough flexibility to launch their attacks. There are also destination side solutions for DDoS attacks such as BGP blackholing which do not aim to prevent attacks from happening but to reduce the impact on the victim. Finally, several efforts have taken place to cut the link between the attackers and the victim by taking down the misusable infrastructure such as open DNS resolvers. However, several studies show that their population is consistently of the magnitude of millions [1, 2].
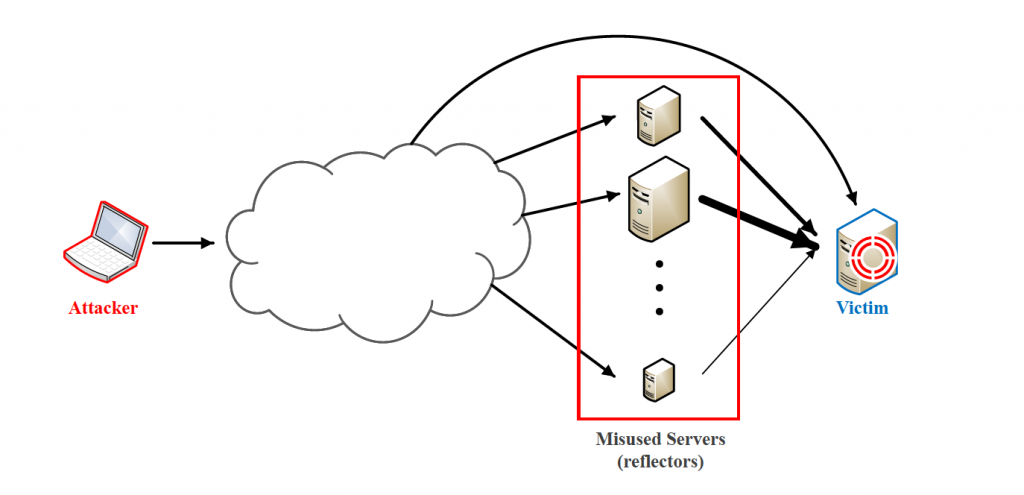
Our intuition tells us that not all reflectors are equally powerful in contributing to a DDoS attack. For example, hosts with high-bandwidth connections are expected to be able to cause more damage to the victim. Datacenter (cloud)-based hosts by design have a high bandwidth. In case of becoming exposed to be misused in DDoS attacks, these hosts would potentially be more appealing for attackers. In our research in progress at the University of Twente, we are investigating the potential share of datacenters in the pool of hosts that are misusable in DDoS attack. Besides we think that some reflectors can provide a higher ampli fication factor due to their internal confi guration, contributing to a higher attack rate. Ultimately, we aim to create a mapping of the reflectors that might be more appealing to be abused by attackers.
By providing a bird’s-eye view of the infrastructure misusable in R&A DDoS attacks, the outcome of this research would yield to an important step in taking countermeasures against R&A DDoS attacks and would give both network operators as well as security research community a better understanding about what we are fighting with.
References
- Shadow Server Open Resolver Scanning Project, https://scan.shadowserver.org/dns/
- Kuhrer, M., Hupperich, T., Rossow, C., Holz, T.: Exit from Hell? Reducing the Impact of Amplifi cation DDoS Attacks. In: 23rd {USENIX} Security Symposium ({USENIX} Security 14). pp. 111-125 (2014)
(By Ramin Yazdani, UT.)
