Encrypted traffic analysis while preserving user privacy
Encrypted traffic is on the rise. In 2016, NSS Labs found out that 97% of surveyed enterprises saw an increase in encrypted web traffic. Both Let’s Encrypt and Google currently report between 70% and 90% of traffic is HTTPS (HTTP encrypted with SSL/TLS). Google has been pressing for HTTPS for a while now. Back in 2014, they started taking into account whether the website uses HTTPS for page ranking, and in 2017 Google Chrome browser started showing “Not Secure” warning in the address bar when visiting websites without HTTPS. In August 2018, Scott Helme, a Security Researcher, analyzed 1 million most popular websites – over 51% are already using HTTPS. According to 2018 The Global Internet Phenomena Report, more than 50% of traffic is encrypted and adoption of new standards such as TLS 1.3 is growing. Gartner predicts 80% of traffic will be encrypted in 2019.
Encryption protects users from invading their traffic and at the same time introduces a blind spot for security tools that can be used to obfuscate malicious activities. There are invasive techniques adopted by some of the enterprises to inspect on encrypted traffic using man-in-the-middle approach by terminating encrypted connections on specific proxies and inspecting on traffic content. Such approach, however legitimate in enterprise environment, cannot be applied in general to inspect traffic of individuals. We contribute to CONCORDIA project in task T1.2 (Network centric security) where we focus on various methods how encrypted traffic can be analyzed for security operations without invading user privacy. One of the techniques that preserves user privacy is based on metadata extraction while encryption is being negotiated. As a result we provide information about version of encryption protocol being used, public key length and algorithm and information from certificate. By processing and analyzing this metadata following use cases can be accomplished.
Cryptographic compliance ensures that only up to date and secure enough encryption algorithms and protocols are being used. Communication is protected based on valid certificates. Encryption metadata also support threat detection. Server name indication enables to distinguish real domain corresponding to user request. Client fingerprint exposed to the network indicates infection with malicious software.
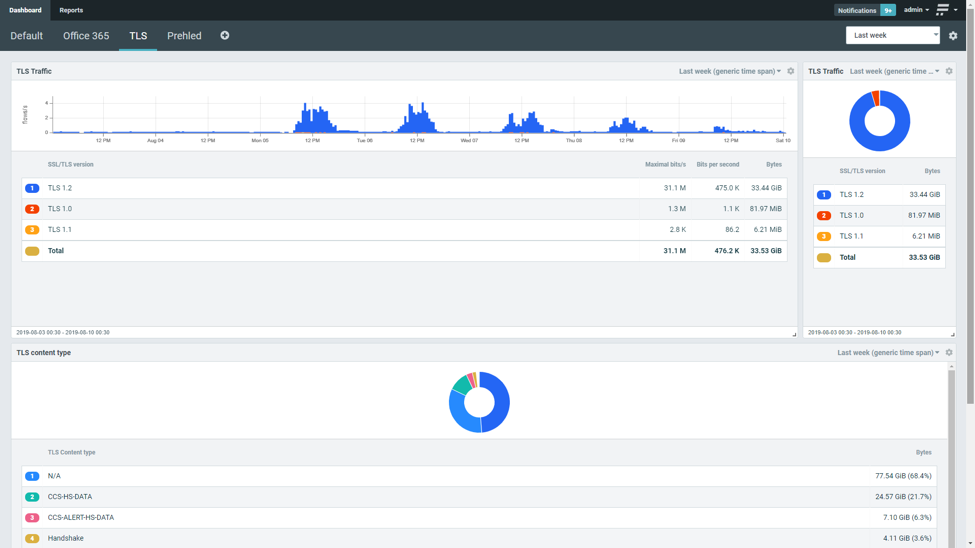
This blog post was prepared at the occasion of general availability of Flowmon 10.3 that provides reporting on encrypted traffic metadata including latest TLS 1.3 protocol. This work has been supported by CONCORDIA project. For more details please contact Flowmon Networks (info@flowmon.com) or visit Flowmon website.
Flowmon is Czech based SME developing a toolset for network traffic monitoring & traffic analysis. Flowmon role in CONCORDIA project is to develop the toolset further for the purpose of encrypted traffic monitoring and metadata extraction (task 1.2 – Network centric security). For the purpose of technology demonstration Flowmon participates telco pilot (task 2.1) with focus on threat detection using industry specific indicators of compromise.
(by Pavel Minařík, Chief Technology Officer in Flowmon Networks)
