Privacy by design: Bringing Machine Learning towards the Edge
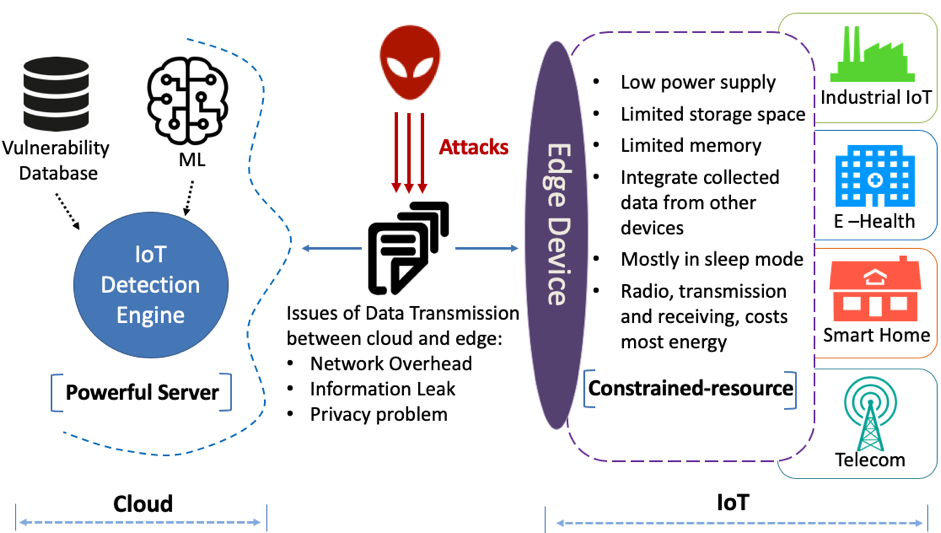
Machine Learning (ML) & Artificial Intelligence (AI) are driven by large quantities of data, which often raises security and privacy concerns (see Figure). With the introduction of new privacy laws, such as the General Data Protection Regulation (GDPR) in the EU, there is a need to conduct R&D on approaches that preserve users’ privacy in the AI era.
One of the research goals of CONCORDIA is to investigate approaches that follow the privacy-by-design principle. RISE and Ericsson are investigating how to reduce the amount of IoT data that is commonly shipped from IoT sources to the cloud by bringing ML/AI closer to the edge of IoT networks. Such an approach would additionally benefit from known edge-computing advantages such as reduced latency/bandwidth and better performance.
There are three main approaches to bring lightweight ML/AI into IoT, mobile, and edge devices:
- Cloud to IoT Edge
Tensorflow Lite (TF Lite) supports converting a model trained with TF on the cloud to the TF Lite model format that can be optimized in model size and performance by post-training quantization techniques. This reduces latency, protects data privacy and reduces power consumption. - Distributed collaborative ML/AI
Federated learning (FL) is a distributed approach enabling edge devices to collaboratively and iteratively train models in a decentralized way while keeping the source data at the devices. Open-sourced libraries and APIs are available to perform secure FL, such as Tensorflow Federated and PySyft. - HW-support for ML/AI
ARM, one of the leading CPU design companies, provides a collection of CPU and memory-optimized neural network kernels as part of the CMSIS standard interface for Cortex-M microcontrollers, for which ARM also supports a TF Lite implementation and the uTensor framework.
Findings
We have analyzed the internals of state-of-the-art ML algorithms and investigated their applicability to IoT security at the edge. We used an analysis methodology that helped us in providing a good estimate on the limitations of constrained devices, which should be useful during an architecture design phase. More details can be found in our recently published paper “Machine Learning for Security at the IoT Edge: A Feasibility Study” [1].
Conclusion
Privacy-by-design can be achieved by off-loading ML/AI processing to the edge. There are several efforts in progress in this space, but overall, they are still at an early stage and are mostly focusing on deep learning methods. In the future, we plan to continue our proposed approach by empirically evaluating and validating our feasibility analysis with performance and accuracy measurements across target devices for relevant security use cases.
References
[1] H. Wang, L. Barriga, A. Vahidi, S. Raza, ” Machine Learning for Security at the IoT Edge: A Feasibility Study”, WISECML, IEEE MASS 2019.
(by Han Wang, Shahid Raza @ RISE & Luis Barriga @ Ericsson)