CONCORDIA Mobile Threat Modelling Framework
A MITRE-based modelling framework for the Telco Industry
Throughout the course of the CONCORDIA project, many partners have showcased and highlighted the importance and advantages of deploying and applying cyber threat intelligence techniques as a way to enhance security practices within an organization. Moreover, efforts between Telenor [1], OsloMet [2] and Ericsson [3] were done to expand this paradigm to the telco sector in order to bring a threat modelling framework that can oversee the impact an attack or an exploit to a device connected to a mobile network can have to both surrounding devices and potentially to the underlying infrastructure. To that end, the CONCORDIA Mobile Threat Modelling Framework was developed.
As this post is a direct follow-up from the previously posted articles in [1], [2] and [3], it is recommend reading them firstly to have a proper overview of the topic at hand.
CONCORDIA Mobile Threat Modelling Framework (CMTMF)
The CONCORDIA Mobile Threat Modelling Framework or CMTMF [4], as shown in Figure 1, is aligned with the MITRE Enterprise matrix and has 14 tactics. The techniques from the Mobile matrix represented by purple boxes are merged with the one of the Enterprise matrices in yellow boxes. The CMTMF includes also the techniques proposed by the BHADRA framework represented by red boxes. Since it is not sufficient with the current techniques, additional CONCORDIA techniques represented by blue boxes have been added.
Currently in this first iteration, the objective is to adapt and grow as the need to accommodate more techniques becomes evident as more attacks become known. Also, the framework goes through continuous updates, the intent is to replace all techniques coming from the first iteration from BHADRA with original ones.
Unlike MITRE ATT&CK, a CMTMF tactic is not unique, instead an attack is documented by phases or stages, for an attack in a mobile network can be a sum of events that are documented by the existing techniques from a specific tactic in different occasions.
An attack in mobile networks can be recursive as it can spread to multiple devices, so the usage of loops is needed to showcase this behavior. This will allow operators to see the true impact of an incoming or detected and in progress attack.
When using CMTMF to model an attack on the mobile network, the aim is to reflect which effects it will have/has had on devices as well as and alongside with the operator’s network infrastructure, giving a unified view of the documented chain of events.
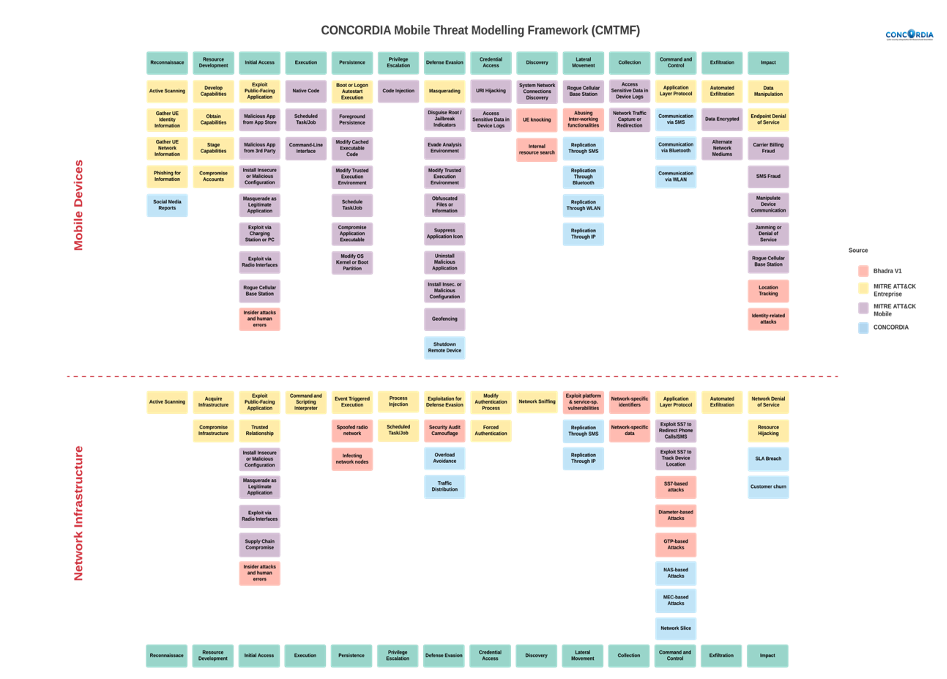
Figure 1 The CONCORDIA Mobile Threat Modelling Framework
Usage of CMTMF
To illustrate the use of the CMTMF, and with the emergence of billion IoT devices in the mobile network, let’s consider a flood attack by IoT devices on the 5G network as it constitutes one of the biggest threats on 5G networks, being essential to model, analyze and find measures to prevent it.
As shown in Figure 2, a flood attack starts on the “Device” stage. The attacker will try to infect and take over control of a large number of IoT devices that are needed for the attack. This stage consists of 12 phases: 1. Initial Access – 2. Execution – 3. Persistence – 4. Privilege Escalation – 5. Defense Evasion – 6. Credential Access – 7. Discovery – 8. Lateral Movement – 9. Collection – 10. Defense Evasion – 11. Command and Control – 12. Exfiltration.
This stage is repeating multiple times until the number of hijacked devices reaches a certain number and the flood attack can now be launched. The “Network” stage can now begin and consists of 3 phases: 13. Command and Control – 14. Defense Evasion – 15. Impact.
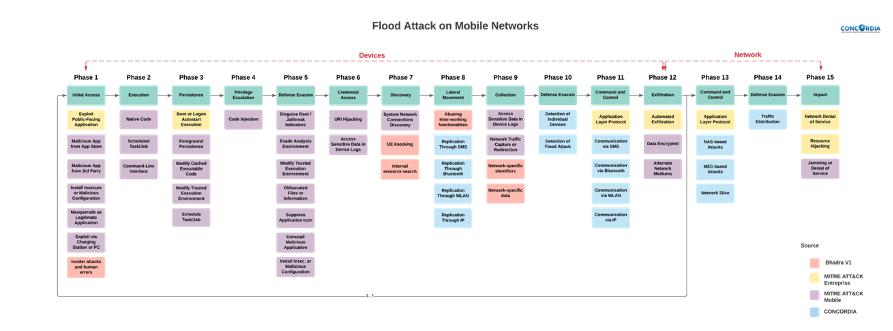
Figure 2 Flood Attack modelled with CMTMF
As mentioned earlier, CMTMF describes and documents an attack by phases, and as it is shown in Figure 2, it is worth emphasizing that the Defense Evasion Tactic is represented twice in the Device stage and once in the Network stage as well as the Command and Control tactic, that is represented once in the Device stage and again in the Network stage.
Integration in MISP
One subsequent and important task was the implementation of the CMTMF in MISP such that threats on mobile network can be shared in such platform, between partners of the CORCORDIA project, and in the near future, between members of the telco community. As of late December 2021, CMTMF is available to all MISP [5] users. This was possible given the close collaboration established with CONCORDIA consortium and CIRCL in Luxembourg.
The process went through migrating CMTMF to the nomenclature used by the platform (Taxonomy, Galaxy, Object and Event), and given all its current tactics and techniques, the framework is now a MISP galaxy. As the framework continues to be expanded and updated, further versions will also be available in the MISP platform.
Combining both CMTMF and MISP workflows, when creating an event (as part of an attack) on MISP, users will have the capability of selecting one or several techniques associated to a tactic, which is now considered as a phase. All relevant information to that phase should be added or extended to that event.
As events/phases are added in MISP, there is a need to establish a link between them so the correlation chain of the documented attack can be seen. To that end, a MISP (meta) object was developed to help determine the phase number (to verify the chain), the name of the attack, the name of the tactic (for the user’s reference) and if the phase will trigger a loop, meaning that that the chain established up to that point will repeat itself. All the elements of this object will allow the MISP user to not only see the full chain of events associated with an attack but also compare with other events and/or attacks that have been shared by other partners.
GUI mockups were created to propose and introduce some additions to the MISP interface so that CMTMF can be easily accessible and to better reflect the proposed interactions in the framework, being one of the relevant changes the correlation graph that will showcase the sequence of an attack described by the documented events, being already available in the latest MISP version and a usage example is shown in Figure 3.
Conclusion
CMTMF comes as a joint effort and collaboration between CONCORDIA partners in order to provide a modelling tool to enhance efforts and to further extend the paradigm of cyber threat intelligence in the telco sector, allowing operators and partners alike to better analyses the ever increasing and expanding attack types that target their infrastructures and the connected devices. Having it available in the MISP platform for general/public usage and having continuous efforts towards its expansion, the long-term prospect is to have CMTMF as a de-facto model for all members of the telco cybersecurity (& sharing) community.
References
[1] Beyond COVID-19 in Threat Intelligence, CONCORDIA Blog, 2021: https://www.concordia-h2020.eu/blog-post/beyond-covid-19-in-threat-intelligence/
[2] Threat Intelligence sharing: What kind of intelligence to share?, CONCORDIA Blog, 2021: https://www.concordia-h2020.eu/blog-post/threat-intelligence-sharing/
[3] Cyber Threat Modelling for Telco, CONCORDIA Blog, 2021: https://www.concordia-h2020.eu/blog-post/cyber-threat-modelling-for-telco/
[4] B. Santos et al., “Threat Modelling for 5G networks,” 2022 International Wireless Communications and Mobile Computing (IWCMC), 2022, pp. 611-616, doi: 10.1109/IWCMC55113.2022.9825149
[5] MISP [Online]. Available: https://www.misp-project.org/
About CONCORDIA
We are a dedicated consortium of more than 50 partners (whose purpose is to lead the boosting Europe’s cybersecurity future. If you are interested in cybersecurity, make sure that you follow us on our communication channels because we will lead its future.
- Website: https://www.concordia-h2020.eu
- Email: contact@concordia-h2020.eu
- Twitter: https://twitter.com/concordiah2020
- LinkedIn: https://www.linkedin.com/in/concordia-h2020/
- Facebook: https://www.facebook.com/concordia.eu/
(By Prof. Dr. Thanh van Do, TELENOR Research, Norway)
