Cyber Threat Modelling for Telco
In previous blogs CONCORDIA partners have been reporting on the various Cyber Threat Intelligence (CTI) aspects that the working groups have been researching [1], [2], [3].
In this blog, we focus on another CTI aspect called Cyber Threat Modelling (CTM). Often when talking about CTI, Indicators of Compromise (IoC) are mentioned as one of the possible data objects, that can be used to identify a threat.
An IoC is roughly a threat signature, such as a malware hash, an adversary’s IP address or a malicious URL. While IoC is a straightforward concept to grasp and manage, CTI platforms can also be used to describe the complete chain of events of a real attack. In other words, CTI also covers the aspect of modelling and sharing adversarial behavior.
One of the most widely used frameworks for modelling adversarial behavior is the MITRE ATT&CK (Adversarial Tactics, Techniques & Common Knowledge) that uses a matrix to describe the sequence of techniques (rows) used to execute tactics (columns) and achieve goals. MITRE ATT&CK has been applied to different technology domains such as enterprise and mobile devices resulting in corresponding matrices that capture known adversarial behaviors within said domains.
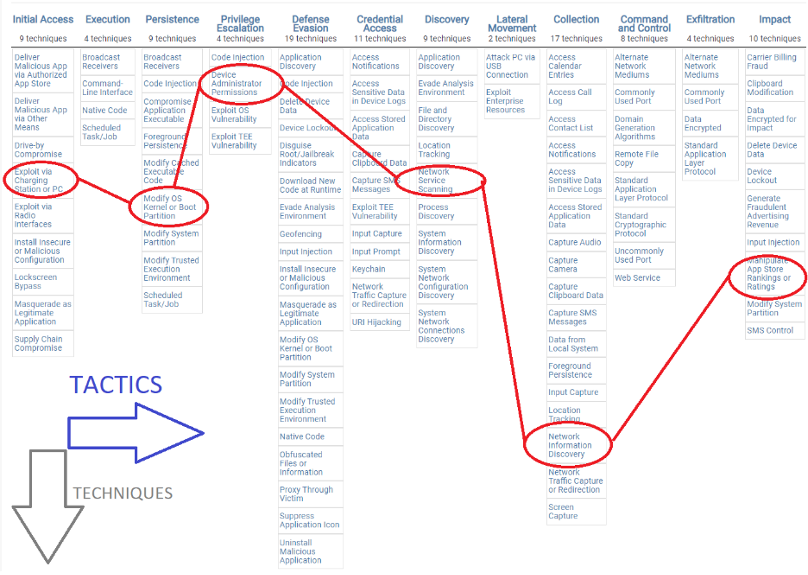
For example, figure 1 illustrates the attack performed to a mobile device whereby the sequence of employed techniques is represented by a chain of connected red ellipses. The mobile device is initially infected using a technique that exploits a device vulnerability that compromises the device upon charging via USB at a rogue charging station. The compromised device is further hacked using another technique that modifies the kernel, followed by more techniques for collecting information about the mobile network and manipulate app stores. Each of the techniques belongs to a tactics category that aims at achieving steppingstone goals towards an ultimate one.
There are ATT&CK matrices for the enterprise and mobile device domains, but there is none for Telecom networks. We believe that for the Telco domain an ATT&CK matrix could be useful in several ways:
- A new class of adversaries – There are different types of adversaries. A user only needs a rooted phone and a SIM card to get access to a mobile network and start attacking it. Adversaries don’t always need a phone and can just develop radio network equipment to conduct radio-level attacks. A mobile operator in a jurisdiction with no business/legal can abuse the interconnection networks to conduct attacks or fraud. As mobile networks are part of most countries’ national infrastructure, some nation states are also potential adversaries. By modelling the behavior of such adversaries, it is possible to design the proper detection and mitigation measures
- Extrapolating adversarial behavior – while understanding the adversary helps in defending against known attacks, the matrix can be used as a baseline help in developing new possible adversarial behavior.
- Penetration testing – A telco matrix can guide operators to simulate attacks and assess the robustness of their networks identifying vulnerabilities
- Risk assessment – a telco matrix can be used during the risk assessment process that operator must conduct regularly as part of the operations. Operators can assess how they has managed the different threats in the Telco matrix.
- Sharing and enriching threat models – by properly describing the complete attack behavior, with the necessary contextualization, enrichment and defenses, operators can exchange this information across the Telco community and contribute to the overall security of the global telco industry.
In the CONCORDIA Telco team, we noticed that when attempting to describe threats to the Telco domain using the available enterprise and mobile device ATT&CK matrices these were partially suitable. Some of the techniques and tactics were applicable, but there were also differences as mobile networks and enterprise networks have totally different trust and threat models. Also, the mobile device matrix mainly covers the device side and not the mobile infrastructure.
We reviewed some prior art proposing a comprehensive ATT&CK matrix for Telco, but we found it oversimplified and incomplete to cover complex threats in cellular mobile networks, especially for new threats coming from industry use cases supported by 5G. The Telco threat landscape is also evolving, and the challenge is to design an adequate ATT&CK modelling framework that can capture the complex interaction between new type of devices, new 5G network technologies, new supported use vertical cases and upcoming generation of mobile networks.
To show the complexity of modelling a threat in Telco we will show an example of a potential threat from the cellular IoT domain as described in the 3GPP TR 33.861 where it is mentioned that low-end low-security cellular IoT devices are likely to be massively deployed, and they could be compromised and used for DDoS and flooding attacks disrupting mobile network services. To model the adversarial behavior of such attacks the following tactics and techniques would be employed:
- Preparation – adversaries would do some homework identifying cellular vulnerable IoT devices that use non-secure software, OS or hardware components.
- Resource Development – adversaries develop or obtain tools to attack IoT devices, deploying C&C center, keeping a library of exploits per device, port scanners, automated password guessing tools, collecting commonly used passwords in IoT devices or exploits to enter the device. Even IMSI catchers can be used to identify devices or false base stations to attract devices to camp and being scanned.
- Reconnaissance – adversaries conduct market analysis of the penetration of vulnerable devices in different geographic areas looking for high-density deployments.
- Initial access – adversaries launch cellular scanners that look for vulnerable devices that once compromised are listed as candidate botnets. The adversary makes of profile of the device CPU architecture, OS and software.
- Execution –adversaries communicate with C&C center via the IoT device to download botnet code turning the device into botnets.
- Persistence & Defense Evasion – once the IoT device has effectively become a botnet, the botnet makes a “hardening” removing any IoT software and services that can disturb it work. The botnet also removes any possible defense mechanism or even competing botnets. The IoT device is not under full control of the C&C center.
- Discovery – botnets start looking for additional IoT devices in the geo-location neighborhood repeating the initial access techniques. IoT devices report their geo-location.
- Command & Control – the botnet uses encrypted communications, proxies, URLs, SMS to hide its contact with the C&C centers. The C&C centers also change DNS names and IP addresses to avoid detection. Security-by-obscurity techniques are also used to keep the hidden communication with the botnets.
- Impact – Under the C&C control, and by having the geo-location of all botnets, the adversary can launch targeted geo-location network attacks such as DDoS or flooding.
As it can be seen from the attack description, while the tactics and some of the techniques resemble the ones used in enterprise and mobile, there are new techniques that are mobile specific. Even the sequence of tactics is a combination of network and device ones. Based on this and other mobile-specific use cases, we are currently developing a telco ATT&CK threat modelling framework. Stay tuned for a follow-up blog describing our findings and results in more detail.
(By: Dr. Luis Barriga, Ericsson, Sweden & Prof. Dr. Thanh van Do, TELENOR Research, Norway)
