How 5G can leverage Cyber Threat Intelligence
Cellular mobile networks have evolved across five generations starting from analogue voice-centric services, going through IP-based mobile services and, today, we stand before the 5th generation that supports various industry vertical use cases requiring enhanced mobile broadband, massive IoT and critical communications.
Along with each generation, the threat surface has also been increasing with adversaries becoming more powerful conducting sophisticated attacks such as tracking users, planting false base stations or compromising IoT devices to use them as botnets for DDoS. The security community has been contributing with threat analyses and ethical hacking revealing unforeseen risks and vulnerabilities in implementations or deployments.
Security in mobile networks has also evolved incorporating technologies to protect users’ security and privacy and to protect network communications, monitor availability and provide resilience. 5G also includes a new assurance framework to provide trustworthiness based on well-defined processes for auditing product development and telco equipment. AI/ML-assisted network security functions can be used to prevent or detect advanced threats.
On the other hand, in CONCORDIA, one of the major topics being investigated is how to use Cyber Threat Intelligence (CTI) in various sectors based on the open-source, widely-used MISP platform. While there are several definitions of CTI, in this article we see CTI as a framework that allows enriching, structuring and exchanging threat information, including action-oriented advice, within a given domain, e.g. telco, healthcare, automotive or finance. Threat information includes context, indicators, mechanisms, consequences and if available adversaries’ profiles, their tactics, techniques and procedures.
So, if 5G systems are collecting telco threats, and CTI offers standard mechanisms for structuring, exchanging and taking actions on threats, how can 5G benefit from CTI?
5G Networks
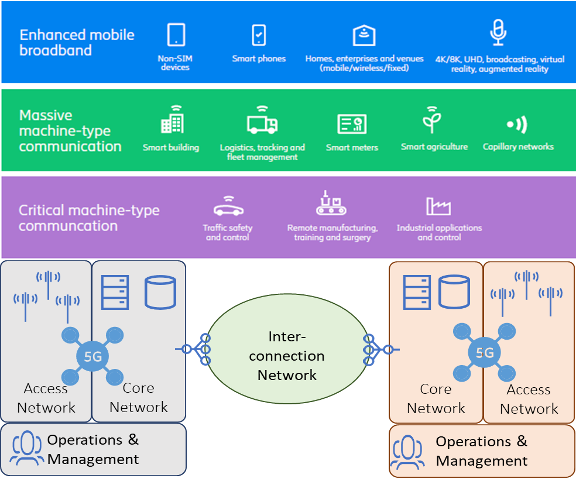
Picture 1 illustrates a conceptual view of two deployed 5G networks supporting different types of industry verticals. A 5G network consists of access radio network and core network that is connected to a peer 5G network via an interconnection network. In addition to the data plane that transports subscriber traffic, both access and core network include a control plane that among other handles functions such as subscriber authentication, key management, mobility management, network exposure towards other networks and AI/ML-based network data analytics. During operations each of these 5G networks is managed by the so-called Operations, Administration & Management system that monitors the performance, availability and security of the networks.
Cyber Threat detection
One of the functions of the Operations, Administration & Management (OAM) system is to monitors the security of the 5G network via the Security Operations Center (SoC). Figure 2 shows how detected threats are reported to the SoC/OAM where further analysis is done, and the necessary mitigation measures are taken.
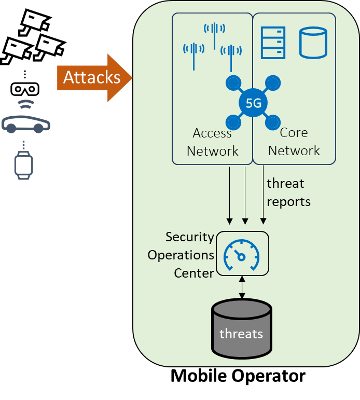
Information about detected threats is stored in a threat repository. For example, if a misbehaving device has been detected, the corresponding threat information can include device/subscription identifiers, IP-addresses, geo-location information, timestamps when attacks have been observed, attack duration, types of attacks, attacks sources etc. Additional information can include the adversary actors behind the attacks and correlation with similar attacks by the same adversary.
Cyber Threat Intelligence challenges for Telcos
So far, the discussion has been in the single-operator scenario. A multi-operator scenario results in a more complex situation that opens for new opportunities and challenges:
- Wouldn’t it be valuable to share such threat intelligence with other operators that could potentially be affected by the same telco threats?
- Assuming some operators have been affected by the same threats, wouldn’t it be useful to compare their collected threats around the same attacks?
- How should home and visited operators collaborate when a group of roaming IoT devices starts misbehaving? Is all information available at the visited operator from the home operator to be able to detect misbehaving devices?
- Once a roaming IoT device has been detected as misbehaving what information shall be kept at visited and home operator’s SoC? Should operators also consider exchanging the actions that have been taken to mitigate the risk?
- Should the home operator share threat intelligence with other operators providing coverage in the same area location to prevent them from being affected? Alternatively share actions to take in case the attack is imminent.
An architecture for 5G Cyber Threat Intelligence
In CONCORDIA we have been investigating how the MISP Cyber Threat Intelligence (CTI) platform could be used to enable sharing CTI information across operators. Picture 3 illustrates how a high-level architecture achieves this goal.
In order to address the challenges described previously, threat information would need to be turned into CTI by enriching, contextualizing and structuring the information in a standard format with enough information that can help other operators to prevent/detect said threats. Sensitive information would need to be filtered out or anonymized if needed.
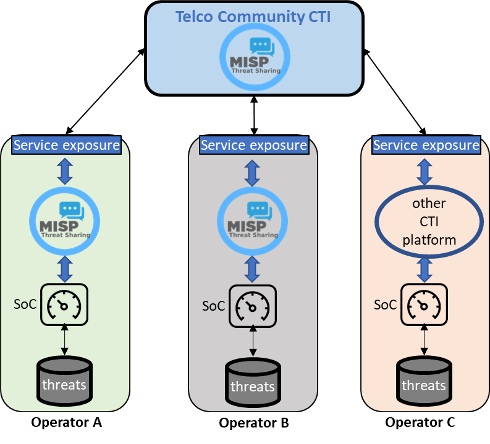
Here is where standard CTI platforms can be of help as they can maintain structured information and has support for standard protocols to exchange threat intelligence information with other operators via a central Telco Community CTI platform. Exporting CTI could be done via standardized 5G service exposure functions. An operator can also use its CTI platform to import threat intelligence information from other sources collecting Telco CTI either to prevent new threats or to enrich and triage existing ones.
We have mentioned that MISP is an open-source readily available CTI platform, but other CTI platforms can be used. There are emerging standards such as STIX (Structured Threat Information eXpression) and TAXII (Trusted Automated Exchange of Intelligence Information) which can be used for interoperability purposes. Even incident response techniques, in the form of playbooks showing how to mitigate given threats, can be exchanged via CTI platforms.
Certainly, only threats that are relevant to expose and share would be exchanged. Another advantage is that an operator can have full control over the threats that can be shared with other operations and the threats that should be kept internal. All the necessary legal constraints need to be respected and the privacy best practices should be followed when sharing information across jurisdictions.
Conclusion
5G mobile networks are considered a critical infrastructure asset in many countries already using a multi-layered defense for risk management purposes. Using CTI for automated exchanged of telco threats would add one defense layer for efficient and cost-effective prevention of threats. We have described how the 5G service-based architecture could benefit from CTI platforms in order to share valuable CTI information across operators for the benefit of the global Telco community.
(By Luis Barriga, Ericsson)
