Cybersecurity in the financial sector – part II
In our last post about Cybersecurity in the Financial Sector we presented some of the main threats to which the financial services entities are exposed, and we concluded about the relevance of cyber-threat intelligence (CTI) sharing tools in order to react fast to several types of cyber-attacks that can affect the entities and their clients.
For that reason, in the CONCORDIA Financial Pilot, we are especially focusing our efforts on integrating a threat intelligence platform based on MISP but integrating financial sector-specific enhanced built-in functionalities, like Indicators of Compromise (IoCs) validation, contextualization/enrichment, and prioritization. It will take into consideration the specific requirements, characteristics and KPIs (Key Performance Indicators) extracted from the finance sector, for the resource optimization, effective detection and appropriate and fast reaction against cyberattacks, whether those are aiming at the bank infrastructure or directly to commit fraud on the clients’ accounts.
Although CTI sharing is widely promoted today and there are many tools and techniques available to enable sharing, in many cases companies are reluctant to share CTI (attack such as tactics, techniques and procedures (TTP), IoCs, IP’s domains, Mule bank accounts, etc.) for a number reasons e.g. they may perceive there are many ‘free-riders’ in sharing infrastructures such as Information Sharing and Analysis Centres (ISACs). While current CTI platforms address the general issue of sharing CTI there are still trust and privacy barriers to overcome to enable greater use of ISACs e.g. such as those associated with so-called ‘free-riders’.
In addition to privacy and trust issues problems exist relating to the quality and granularity of the shared data i.e. the data is not actionable. The CTI is often low level and lacks the necessary contextual attributes to determine the real significance of the threat. Clearly the value of shared CTI would greatly increase if “tactical context” CTI could be added to information that is currently shared. Moreover, in order to effectively handle incidents of a financial fraud it is necessary to know the behaviour of the attacker, not only from the fraud suffered by a bank or financial institution, but also from the frauds suffered by other institutions. Therefore, sharing the applied fraud strategies expressed as TTP’s can be of great value for all financial institutions.
Sharing CTI about adversary attack strategies and techniques can yield much benefit in the fight against cybercrime e.g. for financial services the sharing of the strategy (1) applied in carrying out a fraud, the tactics that the attacker applies, as well as the techniques used, are of great value for all financial institutions. As an example, this approach would allow the emulation of well-studied financial sector threat actors such as Cabarnak /FIN7(2) .
Therefore, the work planned in CONCORDIA for the development of a Financial Threat Intelligence Platform will encompass some of the following tasks:
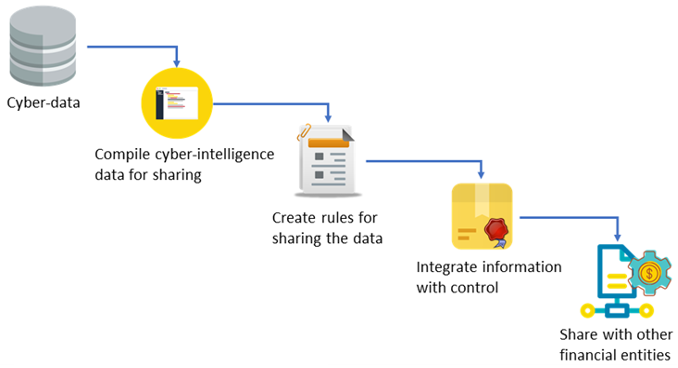
- Build a cyber-intelligence sharing platform especially adapted for the needs of the financial sector o Define the required type of information by the financial entities, not only related to cybersecurity assets, but also fraud prevention IoCs.
- Search and define lists of sources of cybersecurity for the financial sector.
- Create tools or solutions for obtaining a more useful intelligence from the sources (either from cybersecurity organizations or others such as Social Networks).
- Design and develop Cyber-intelligence Sharing Agreement. Define rules, roles, and policies for sharing data, by means of privacy and access control mechanisms that allows to specify who can access the information, the validity of the data and which users or entities can access it.
- Create a framework that allows a user-friendly way to share cyber-intelligence of the financial sector with other entities.
Nevertheless, the objective of the pilot is not to create another CTI platform from the scratch, but to build the solution over existing technologies widely used such as MISP. Indeed, it is also aligned with CONCORDIA vision of a European Threat Intelligence platform using MISP, through which a network of cross-sectorial industries and administrations will be able share actionable cybersecurity IoCs and help each other to be react as fast as possible against potential attacks.
(By Ramon Martín de Pozuelo – CaixaBank, Jose Francisco Ruiz – ATOS)
References:
- See e.g. MITRE ATT&CK analysis of one such financial services adversary, Carabank – https://bit.ly/2YqoDuK.
- https://attackevals.mitre.org/carbanak-fin7/