(Emerging) digital identity models and their impact on user-centric security
According to Kim Cameron[1](Chief Architecture of Identity from 2004 to 2019 at Microsoft), the Internet – as we know it today, was built without an identity layer. Moreover, the World Wide Web inventor, Tim Berners-Lee, recently started a new project named Solid[2], to radically change how the Internet works today – by introducing a new digital identity layer. Why do such renowned names of the Internet space nowadays rethink the Digital Identity area’s problems/issues? In this post, we will briefly review and present currently available digital identity models with a goal to better (try to) understand why the identity layer is so important.
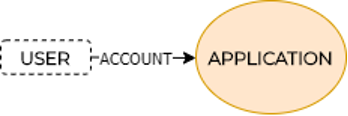
TRADITIONAL (CENTRALIZED) IDENTITY MODEL
Probably the most utilized model, where each individual (i.e., user) has an established account with each internet application (e.g., website, service, etc.). Typically, users register an account (i.e., create a digital identity in the scope of application) with an associated username and password. The information about digital identity is fully stored and maintained by the application (provider). Whenever the users use an application, they need to authenticate themselves to an application provider. In such a process, the users are borrowing digital identity (representing them) from the application. As already mentioned, these credentials are owned by the application provider and not by the user (Preukschat & Reed, 2021).
Moreover, most applications demand a new registration, wherein it is important to notice that application providers have their security and privacy policies. One of the main obstacles for the end-users is that none of the previously created digital identities is reusable, i.e., portable to any other application. Each digital identity exists only in the scope of each application. So the users manage but do not own the usernames and passwords of each digital identity – which can be a complex task. Suppose we assume that the users are aware of how dangerous password reuse is, then: n-applications demand n-digital identities, resulting in one user manages n-different passwords. Typically the metadata of those digital identities includes some personal data, which are usually stored within centralized databases (on the application provider side) where they present a massive honeypot for hackers (historically confirmed[3]) (Lesavre, Varin, Mell, Davidson, & Shook, 2020; Preukschat & Reed, 2021).
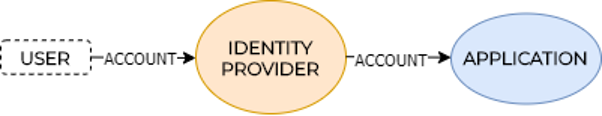
FEDERATED IDENTITY MODEL
Some enterprises recognized a centralized digital identity model for the end-users – mostly those related to the complexity of managing multiple accounts, i.e., passwords. Consequently, a new – federated digital identity model has been developed where the identity provider role is introduced. The role of the identity provider is to provide digital identity services to the applications. With this model, the users can control only one digital identity, i.e., an account with an associated username and password, and reuse it within multiple applications. The digital identity is registered/owned/stored on the identity provider side (not application provider anymore). In such a digital identity model, the user authenticates himself to the identity provider and later uses this one digital identity within multiple applications (if they support this model – nowadays also known as Single Sign-On – SSO) (Lesavre et al., 2020; Preukschat & Reed, 2021). Again, as in the previously described digital identity data model, the digital identities (with metadata) are usually stored within some centralized databases (on the identity provider side), where they present a massive honeypot for hackers (again – historically confirmed[4]). However, some important concerns persist. The most interesting is the following “provocative” question: Who owns your digital identity (and all related metadata), and do you (as a user) trust this identity provider?
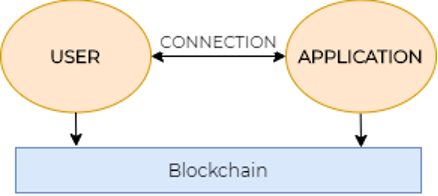
DECENTRALIZED IDENTITY MODEL
DECENTRALIZED IDENTITY MODELMotivated by emerging technology, i.e., blockchain technology, a new – decentralized digital identity model appears. This digital identity model entirely relies on cryptography, i.e., decentralized public key infrastructure. The users are now no longer forced to register their digital identity (i.e., account) at the application (provider) or identity provider side. The users can now generate a cryptographic public-private key and create their own digital identities. Later they can register the identifier (i.e., decentralized identifier[5]) of this digital identity on some trustless infrastructure (e.g., distributed ledger) to reuse this digital identity. Then, the users can authenticate themselves to multiple applications – because now they can cryptographically prove that they control (and owns) the private key of the registered identifier related to the digital identity. Unlike the previous two described digital identity models, the digital identity is now fully owned by the users.
Consequently, users’ privacy is enhanced – since there is no need for the users to trust any other third party that their digital identity (e.g., application provider, identity provider) is appropriately managed. The decentralized identity model is usually also related to the nowadays hot topic term “Self-Sovereign Identity” (Lesavre et al., 2020; Preukschat & Reed, 2021). This model’s main novelty is that the users fully own their digital identity, and only they choose to whom the data related to their digital identity is shared. However, some new (old) issues appear, such as the Public-Key cryptography usability for the users involving the storage of private keys, digital signing process complexity, etc.
CONCLUSION
In Concordia, the University of Maribor research team, among other activities, also participates in T1.5 – “User-Centric Security,” where our activities are related to investigating how the digital identity models above can be further improved to secure user. Besides, we are also exploring where and how to apply the new digital identity models, including the possibilities to consolidate some of the currently widely accepted digital identity model concepts with the principles of newly emerged digital identity concepts. We are also investigating how emerging technologies (i.e., blockchain technology) can combine with existing Connecting Europe Facility (CEF) building blocks (e.g., eID, eSignature, CEF EBSI, etc.), and thus enable secure, privacy-preserving usage of internet services to the end-users (Turkanovic & Podgorelec, 2020).
REFERENCES
Lesavre, L., Varin, P., Mell, P., Davidson, M., & Shook, J. (2020). A Taxonomic Approach to Understanding Emerging Blockchain Identity Management Systems. Retrieved from https://www.nist.gov/publications/taxonomic-approach-understanding-emerging-blockchain-identity-management-systems
Preukschat, A., & Reed, D. (2021).
Self-Sovereign Identity: Decentralized Digital Identity and Verifiable Credentials: Manning Publications.
Turkanovic, M., & Podgorelec, B. (2020).
Signing Blockchain Transactions using Qualified Certificates. IEEE Internet Computing.
[1]https://www.infoq.com/news/2018/10/solid-identity-platform/
[2]https://solid.mit.edu/
[3]https://www.zdnet.com/article/adobe-left-7-5-million-creative-cloud-user-records-exposed-online/
[4]https://fortune.com/2016/05/18/linkedin-data-breach-email-password/
[5]https://www.w3.org/TR/did-core/
(By Blaž Podgorelec, University of Maribor)
