Make Digital Work, not just Function
Security, Privacy, Trust & Trustworthiness, by Design
Misalignment Nr. 1
There still is huge misalignment between the economics of selling technology, products, systems and services, and the economics of security, privacy, trust and trustworthiness.
On that, the Head of Europol’s Cybercrime Centre (EC3), Steve Wilson, for instance stated the following:
‘If people are unaware of the threat then they’re not going to ask questions regarding this. What we’ve got to do is raise that awareness amongst consumers, then people will start asking the questions.
Then, vendors will design goods to a certain minimum of standard and the consumer will seek that out rather than seeking something out that’s cheaper, but doesn’t have security.’
‘Globally, we have a very poor understanding of the economics of cybersecurity. There is a business case to flood the market with insecure devices, unfortunately – but people make a lot of money out of it.’
Misalignment Nr. 2
The other misalignment in this Digital Age is an engineer, manufacturer, vendor or services provider claiming that ‘it works’ while such claim is generally only referring to the features and functionalities.
The non-functionalities are seldom being into account. What if it does not work as exactly intended? Cybersecurity, safety, privacy and nowadays also digital sovereignty, resilience and trust are those non-functionals that should, by design and by default, be part of any truly ‘working’ technology, product, system and service.
These non-functionalities are generally still seen as a mere after-thought, an engineering nuisance and cost-adding factor. However, given the pace at which technology has developed and is developing, state-of-the-art cyber security and related resilience are not nice-to-haves anymore. They are absolute need-to-haves.
Meanwhile
Meanwhile, people, society, public and private sectors have become over-dependent on these undependable systems.
Recently, related to this topic Commissioner Breton stated the following, with the title ‘Europe: The End of ‘Naivety’’ [1]:
‘We will also strengthen the protection of our information space, which is still too largely dominated by non-European geo-economic players, and establish the legal framework for a single European data space. Europe missed the first wave of the personal data economy. It will not miss the enormous potential of industrial data that is whetting the appetite of the GAFAMs and other BATXs. We are also working to secure our 5G networks, because our critical infrastructures cannot be vulnerable.
And we are finalising a new cyber security strategy – a “European Cyber Shield” – to take into account the arrival of billions of connected things, from cars to children’s toys, healthcare devices and household appliances. Industrial data, 5G, cyber security and computing power will condition our sovereignty for decades to come.’
How to Make it Work?
The Why is clear to all. The How is where most struggle and stop. How to make things work, also when they do not function as intended?
Taking and keeping cybersecurity and other trust principles by design into consideration and in continuous operation mode, as well as otherwise converting that talk to an effective and useful walk by design, by default and continuously are easier said than done.
For instance, try to elaborate about these questions, and think about finding the right balance of values and interests:
- How are you and your organisation currently consider and implement cybersecurity and related principles?
- How do you balance out the various cybersecurity principles, safety principles, privacy principles, data management principles, and other trust principles?
- How to control and dynamically assure complex IT, OT, IoT or other cyber-physical (eco)systems and their many chipsets, components, connectivity, sensors, algorithms, data flows, APIs, patches, users and other actors, when most has been procured from third parties?
- And, who is willing to, or otherwise going to pay for all this?
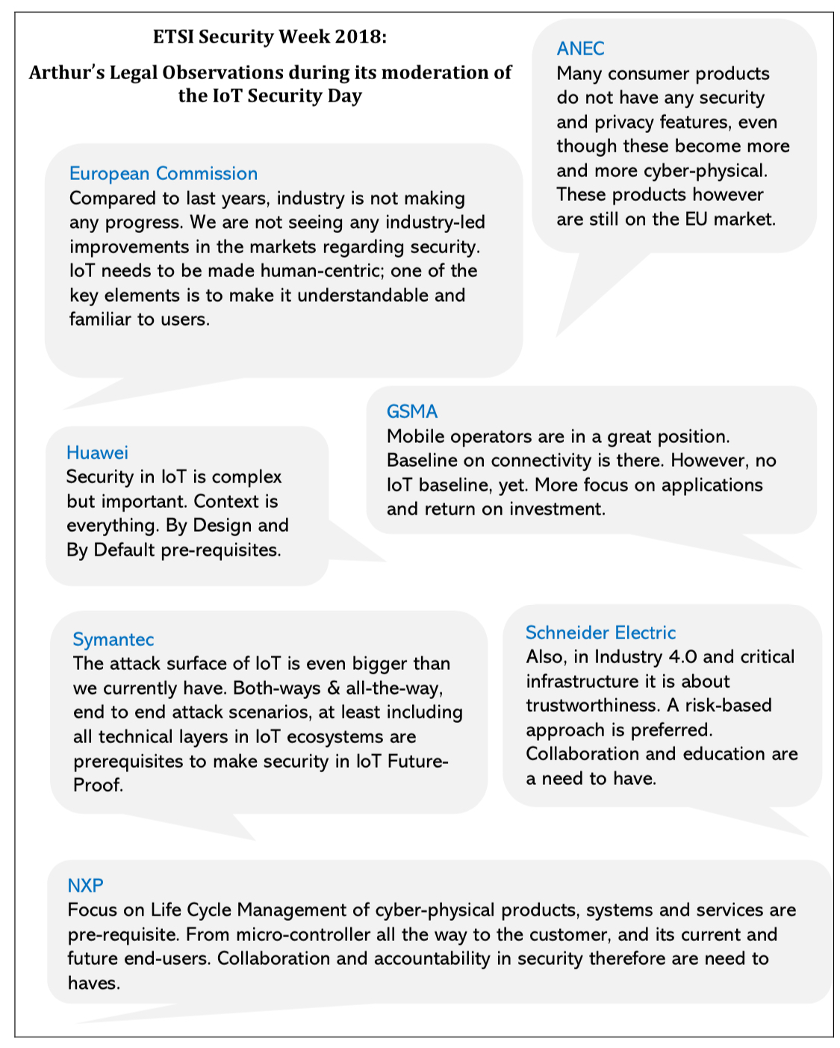
That these dilemmas are truly complex ones, and it a struggle that needs coordination, orchestration and system-leadership can for instance easily seen in the quotes below while discussing at ETSI in Sophia Antipolis with cybersecurity experts and other professionals from around the world about security in IoT ecosystems:
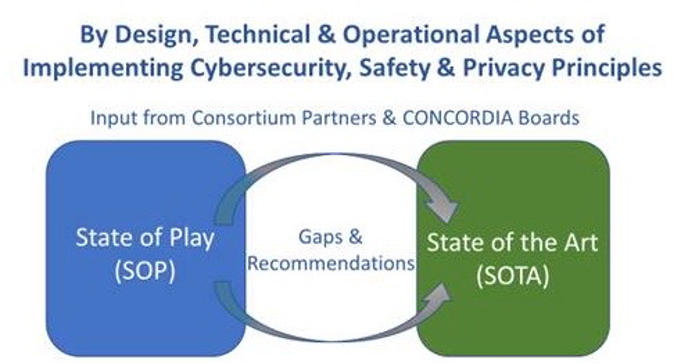
At CONCORDIA, these and other balancing acts and related dilemmas are fully on the radar, including how to effectively address and organise those in view of the proposed European Cybersecurity Competence Center structure [2], which is part of the European Cyber Strategy [3]. CONCORDIA is aiming to contribute to, and enable and facilitate the desired system-leadership in these essential domains in the Digital Age.
This, as CONCORDIA does not see these dilemmas as mere challenges but also as huge opportunities, both for the European Union and its market, sectors, society and economy, but also as a trustworthy export capabilities, kindly powered by the many EU omnistakeholders, for the benefit of global citizens, society, ecology and economy. If you re-read the quotes set above of Commissioner Breton with that perspective, you still feel the passion but also the believe in a future full of opportunities:
- for research and education;
- for education, skills and jobs;
- for innovation and economic development, and;
- for resilience and sovereignty.
These four segments – in contextual symbiosis – are the main drivers of said European Cybersecurity Competence Center structure, and therefore also the drivers of CONCORDIA.
The How is about making things concrete, transparent and understandable. The more practical and operational we can help make Security & Privacy Principles, the easier for designers, engineers, manufactures to embed those in designs, prototypes and production environments, and the easier those can be tested, certified and continuously improved. It is all about Trust & Trustworthiness By Design & By Design, and thereafter never stop taking care of those after deployment.
For these purposes, in the next period we will for instance initiate various interviews with cybersecurity experts to discuss these practical and otherwise operational queries, representing industry, academia and competent authorities both at national and European level.
Because, let’s face it: cybersecurity is not a problem. It is a prerequisite part of the solution to demonstrate trustworthiness and build and sustain trust. But if we are not willing and able to make it as practical as possible, we will never bridge the Talk towards the Walk. And we will never Walk the Walk.
So, let’s address non-functionals such as cybersecurity, safety, privacy, trust and the like as integral part of functionality. Let’s make digital work for all, without any surprises.
(Blog by Arthur’s Legal, Strategies & Systems 
References:
[1]Europe: The Keys To Sovereignty, by Commissioner Breton, 11 September 2020: https://ec.europa.eu/commission/commissioners/2019-2024/breton/announcements/europe-end-naivety_en.
[2] Proposal for a Regulation of the European Parliament and of the Council establishing the European Cybersecurity Industrial, Technology and Research Competence Centre and the Network of National Coordination Centers: https://ec.europa.eu/digital-single-market/en/news/proposal-regulation-establishing-european-cybersecurity-industrial-technology-and-research.
[3]EU Security Union Strategy, including an overview of all relevant initiatives: https://ec.europa.eu/digital-single-market/en/cyber-security.
If you would like to get involved and learn more
about cybersecurity and related matters, make sure
that you contact or otherwise follow CONCORDIA:
https://www.linkedin.com/in/concordia-h2020/
https://www.concordia-h2020.eu