Countermeasures and Research Actions
COVID-19 has increased reliance on information technologies in all aspects of life, creating new gaps and exacerbating existing ones, making us more than ever vulnerable to new and already existing security threats. As a first thing, in https://www.concordia-h2020.eu/blog-post/threats-gaps-and-challenges-in-the-era-of-covid-19/ we identified the most relevant threats, gaps, and challenges, with particular reference to the COVID-19. Here,
we summarize the countermeasures addressing such threats and highlight the corresponding directions for future research. We consider classes of countermeasures based on the current trends, according to the six domains of interest of CONCORDIA (Device/IoT, Network, System, Data, Application, and User) as well as cross-domain solutions.
Device/IoT
A number of traditional and novel countermeasures need be considered to ensure security of IoT devices. They should be implemented with the best security practices (e.g., compartmentalization), and patched prior to their release. The resource-constrained nature of IoT devices calls for novel approaches to prevent malicious activities, including lightweight cryptographic algorithms, monitoring through intrusion detection systems (IDSs) based on artificial intelligence (AI) and machine, as well as regular maintenance and updates. Moreover, additional regulations and policies, such as the IoT Cybersecurity Improvement Act 2020 are necessary to ensure guidelines and transparency for both the developers and end-users. Future research actions should focus on:
- ML/DL-based solutions: solutions based on ML and deep learning (DL) can mitigate privacy and access control issues, boost attack and intrusion detection capabilities, malicious code identification and malware analysis.
- Blockchain-based solutions: the main properties of blockchain, including immutability, verifiability, and efficiency can aid in preventing attacks and help vendors in defining configuration standards.
- Novel authentication schemes: lightweight authentication schemes and protocols should be designed to accommodate IoT devices peculiarities, such as resource constraints and scalability to manage large number of devices
Network
Countermeasures in the network domain should ensure security assurance to the network components, thus certifying that a particular product has been designed and developed with a specific level of security and is compliant to the standards. This implies that supply-chain risk assessment
and product testing should be practiced, and vendors should offer appropriate security protection and be responsible for security lapses. Additional countermeasures include strictly following state-of-the-art practices and guidelines in terms of activation of security features, hardening of the configuration, network segmentation and protection of internal interfaces from external access. Moreover, automation and machine learning should be integrated into network operation and management processes. Timely patching of known vulnerabilities and security updates should become common practice for reducing exploitation risks. Future research actions should focus on:
- AI and ML-based solutions: AI and ML-based solutions have potential in a wide array of network activities, including service orchestration, demand management, security response and analytics. They can enhance security tools’ capabilities in terms of speed of identification of potential threats, enabling faster mitigating reactions. AI-based network-monitoring tools can also be used to track users’ behavior and detecting anomalies in it, allowing cybersecurity teams to respond in an intelligent way and in real-time.
- Quantum Safe Cryptography: quantum safe cryptography and similar paradigms (e.g., Quantum Key Distribution) can increase the continuously-diminishing security of the communication channels. An emerging research topic is Quantum machine learning, that is, the
integration of quantum algorithms within ML. This technology can utilize qubits and quantum operations or specialized quantum systems to improve computational speed and data storage of ML algorithms
System
There are several notable countermeasures that have to implemented to ensure security and protect the data integrity of VMs and clouds. Hypervisor firewalls should be enabled to protect VMs by monitoring their activities and separating good from malicious traffic, while internal firewalls can control both public and private network traffic within and outside the cloud. The protection of data in a virtual environment should be carried out in three phases, namely data-at-rest, encryption of data in-transit, and encryption of data on backup media. Granular access control and internal and external authentications should be deployed to mitigate compatibility issues of private and public clouds. Lastly, both VMs and operating systems have to be properly hardened and regularly monitored, while every system should be designed with at least minimum security
requirement satisfied. Future research actions should focus on:
- SDN: SDN-based cloud solutions, such as multi-clouds, hybrid clouds, meta-clouds, and clouds federations not only increase cloud services’ efficiency but also showcase the potential in differentiating good and malicious traffic.
- ML/DL-based solutions: these solutions can aid the detection of cloud data breaches, in addition to bolster efficiency and reliability of cloud services.
- Data encryption: research on novel concepts such as real-time encryption technology and real-time defensive systems is a promising and flourishing research area to fill existing security gaps.
- Cloud-to-cloud backup: cloud-to-cloud backup is one of the upcoming security solutions that is expected to fix the shortcomings of traditional backup technologies.
Data
Countermeasures protecting sensitive data against data breaches include data masking methods, such as encryption, character shuffling, and character/word substitution, while identity and access management techniques (e.g., multi-factor authentication) can be used to control access to sensitive data within organizations. Moreover, endpoint protection and response techniques are useful to identify data breaches in real-time and lock jeopardized endpoints. Data audits should be performed periodically to identify new gaps. The risk of recovery failure from attacks can be attenuated by deploying data backups in different locations. Finally, intrusion detection and protection systems should collect data about potential attacks bolstering intrusion protection. Future research actions should focus on:
- Blockchain-based solutions: blockchain’s immutability property can grant trustworthiness, auditability, transparency, and integrity of (big) data, while eliminating the risk of data breaches and single points of failure during the process of data movement from the data warehouses to distributed storage.
- Access control and data encryption: popular recent data encryption solutions include data masking schemes, Fully Homomorphic Encryption (FHE), lightweight cryptography variations, and improvements of techniques such as Attribute-Based Encryption (ABE).
- ML/AI-based solutions: current research efforts in this area focus mostly on feature squeezing to reduce the research space available to potential adversaries, whereas the future endeavours should focus on solving issues related to adaptability and robustness of ML models.
- Self-destructing data: future research should consider reliable self-destructing data solutions, in turn complying with privacy requirements
Application
Countermeasures in the application domain consider two main directions, namely the simplification of the security-related maintenance burden on developers and IT admins, and providing improved protection. Recently, the early inclusion of security in the development process has been
increasingly advocated through development methodologies such as DevSecOps. Consequently, already safe and secure solutions play an important role in removing many long-standing issues still affecting the security landscape, thus allowing personnel to focus on sophisticated security aspects. In other words, existing countermeasures are forming the basis on which more sophisticated solutions should be built. Future research actions should focus on:
- Zero Trust (ZT) security: ZT can enhance security by default, in which the physical network perimeter does not coincide with the logical security perimeter. This approach relies on the identity, which represents the only barrier for accessing resources.
- ML/AI-based solutions: AI can improve the state of the art in many sectors where classification tasks are required; however negative AI implications have to be carefully considered.
- Authentication: strong authentication techniques, such as token-based authentication and biometrics require further research endeavours, to design user-friendly solutions for small and medium-sized organizations.
- Supply chain: increasing number of indirect attacks demands the proper investigation of supply-chain security.
User
User-centric security countermeasures have to consider both external and internal threats, while being generalizable to most organizations. Automated tools, such as firewalls and traffic analysis, can be adopted to prevent external attacks. On the other hand, internal attacks can be identified by monitoring network and execution logs, while access control policies, roles separation, multi-factor authentication, and encryption can be used. Finally, security training should be considered a basic prerequisite to reduce human-related weaknesses. The importance of research in the user domain is ever-increasing in an age where information and privacy are the most valuable assets. Future research actions should focus on:
- Security training techniques: improvements on these practices can increase the users’ security awareness and efficacy of the already adopted security techniques, and consequently mitigate an array of threats.
- Fight against disinformation: the spread of disinformation among less educated people in a time of stressful events has worsened the lack of trust in institutions, leading to violent events and non-compliance with health standard.
- Social engineering and user behavior: dissemination of information is making users vulnerable to social engineering attacks, such as persuasion and fraud.
- AI applications for user security: the nature of threats directly targeting users call for of AI-based applications, which may, even, counteract attacks powered by AI
Overview of the Countermeasures
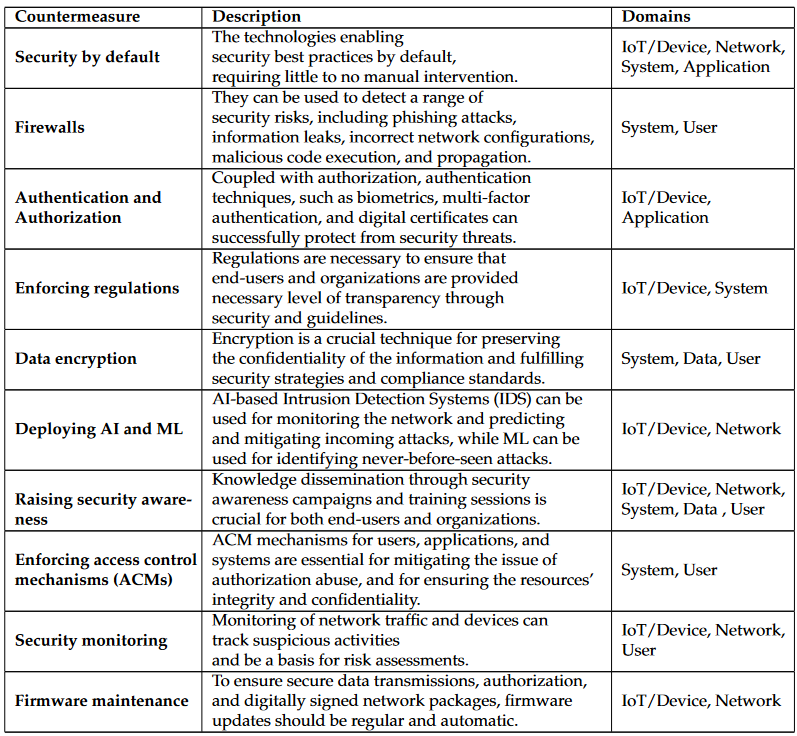
The following table briefly summarizes the most prominent security countermeasures with the respect to the related domains.
Overview of the Research Actions
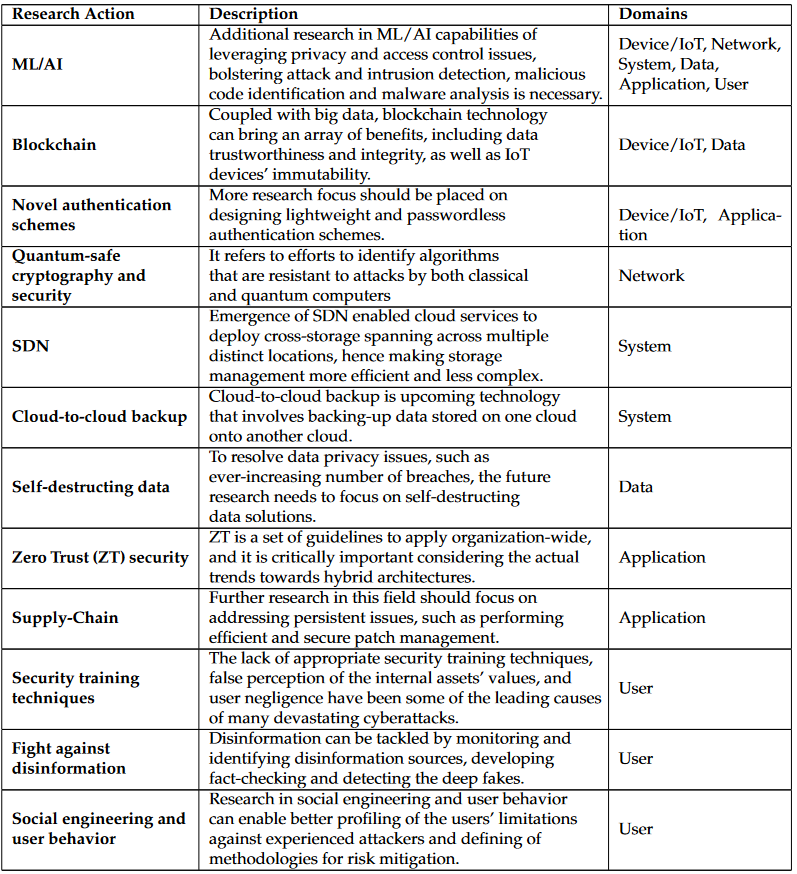
The following table briefly summarizes the most prominent security research actions with the respect to the related domains. These research actions show a great potential for tackling the majority of the existing gaps and challenges; however, they require further research endeavour.
Conclusion
In summary, the ever-evolving gaps and challenges we are facing demand for i) well-established security practices as a first defense, ranging from prompt patches and DevOps methodologies to security training; ii) sophisticated monitoring approaches as a second and complementary defense. 5One of the most promising research trend are in fact solutions based on AI, that however require additional research effort, balancing accuracy and other requirements, such as privacy
(By Marco Anisetti, Claudio A. Ardagna, Nicola Bena, Ernesto Damiani, Jadran Sessa, Università degli Studi di Milano)
