On the Cybersecurity Planning and Investments: An Approach with Economic Bias
Many of the problems plaguing cybersecurity are technical in nature, but they may have an economic motivation (e.g., to obtain financial profits) and certainly, an economic impact. The primary motivation (besides espionage and destruction) behind cyberattacks is making financial profits. On one hand, there are known examples as ransomware attacks request money from their victims to return their data, offering of stolen data in illegal markets, and Denial-of-Service (DoS) attacks, which are commonly used as means of extortion. On the other hand, the companies’ lack of knowledge to assess risks and potential impacts of cyberattacks, is a fact that raises alerts in a worldwide scale. This problem is more prominent in companies that allocate a relatively small budget available to detect and react upon cybersecurity threats. In addition, they typically they lack technical security expertise, which holds especially true for Small- and Medium-sized Enterprises (SME) and micro-companies.
Unfortunately, SMEs frequently neglect approaches to handle cybersecurity issues, primarily due to the lack of economic and technical resources, including insufficient budget, missing personnel skills, and minimal cybersecurity knowledge. Further, many SMEs falsely think that they are not a target of cybercrime. The realistic scenario is exactly the opposite, in which cybercriminals tend to see SMEs as a preferred target due to a higher likelihood of success in the case of a cyberattack. Therefore, it is highly relevant that cybersecurity initiatives, guidelines, and solutions address explicitly challenges SMEs are facing. In this sense, one of the main efforts in the short term involves education and cybersecurity awareness, which are also key to reduce the number of successful attacks against these companies, since expertise becomes available and applicable.
The availability of a framework based on clearly defined steps in which a general approach can be instantiated for specific applications is highly relevant in this scope. In this sense, considering the low expertise concerning specific security concepts, which, nevertheless, often possess expertise at the business level, such a framework allows to (a) reduce the possibility of being a target of cybersecurity threats; (b) increase awareness on the exposure of cybersecurity threats. Thus, (a) it is possible that the application of defined stages allows the establishment of a structured plan for risk assessment as well as for measures associated with risk mitigation. This would imply that (b) awareness about risk exposure would be increased.
Figure 1 exemplifies relevant steps and techniques for an efficient cybersecurity planning and deployment of effective cybersecurity strategies in SMEs. These steps and techniques are summarized and organized as a framework, starting at Phase A, where information related to the business itself is collected, and a briefing is conducted with stakeholders involved. Phase B focuses on the security analysis and threat modeling of this company under investigation. Different approaches can be considered, such as using well-known cybersecurity products and specific penetration tests. Also, specific steps related to the risk assessment with economic bias can be followed, as proposed by the SEConomy framework [1]. Lastly, with the relevant security information at hand, Phase C consists of the definition of cybersecurity requirements, the mapping of processes that must be modified or created within that company, and the definition of educational activities required to implement, deploy, and operate the cybersecurity strategy. After all, the information is mapped, and relevant cybersecurity requirements are defined, e.g., the main goal, acceptable levels of protection, and risks that can be assumed.
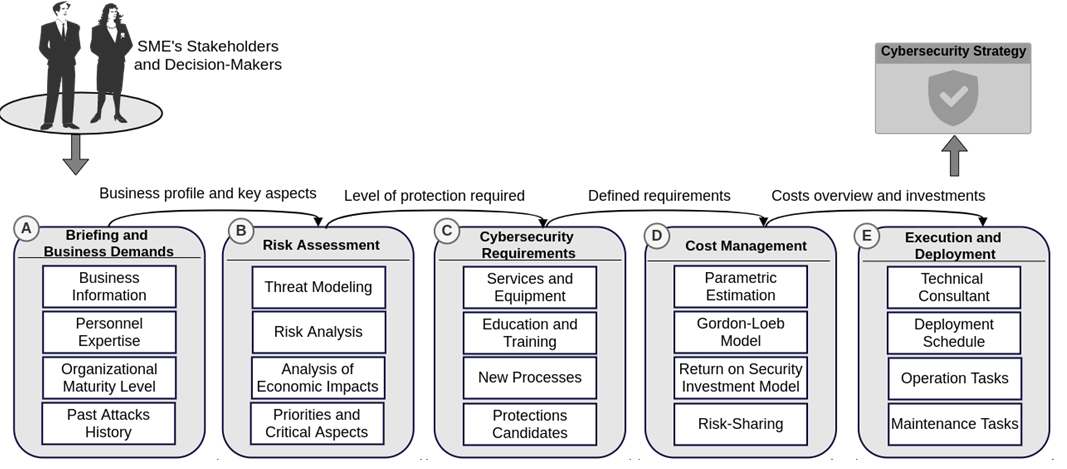
Figure1: Overview of Steps for Planning and Investment in Cybersecurity
Within the Cost Management phase (Phase D), cybersecurity costs are estimated, and the optimum investment amount is defined. For that, cybersecurity economics models can be used, such as the Gordon-Loeb model, to estimate the optimal investment in cybersecurity and the Return On Security Investment (ROSI) to calculate the payback and cost-efficiency of a given cybersecurity solution. The cost management might also consider sharing the risks and reducing economic impacts by acquiring cyber insurance [2]. Finally, the cybersecurity strategy can be deployed within Phase E to protect the company and its supply chain against further threats, thus, reducing the chances of business disruption and financial impacts due to cyberattacks. These steps of the framework do offer structured help to cybersecurity consultants since it is not trivial to obtain all these information without prior experience in that field and the company.
Based on these different needs identified and current market trends, it is possible to identify a demand for approaches that simplify cybersecurity planning and to provide an intuitive way to assess risks and make cost-effective decisions, especially to support the adoption of cybersecurity measures by SMEs. This is the case with SECAdvisor [3], a visual tool developed within the Communication Systems Research Group CSG at the Department of Informatics IfI of the University of Zurich UZH, as part of Christian Omlin’s Bachelor Thesis. The idea and motivation behind SECAdvisor is to consolidate the knowledge obtained along the research and discussions on this topic conducted by the CSG within the European community as part of Task 4.3 “Economics Perspective”, being part of the cybersecurity project H2020 CONCORDIA. SECAdvisor allows to definite information segments within a company and calculate the optimal investment for each segment, including potential losses with and without an optimal investment in cybersecurity. This calculation uses the Gordon-Loeb model and considers security-breach probability functions to estimate values as accurate as possible. After calculating an overview of the amount of funds in cybersecurity, SECAdvisor recommends protection measures. ROSI is calculated for each recommended solution to compare different protections alternatives in terms of payback or cost-effectiveness. Table 1 overviews in an example relevant costs and investments calculated by SECAdvisor for the three determined database segments (especially “Customer”, “Internal Operations”, and “External Operations”). These outcomes are based on the Gordon-Loeb approach and are suggested to be used to guide precise investments in cybersecurity.
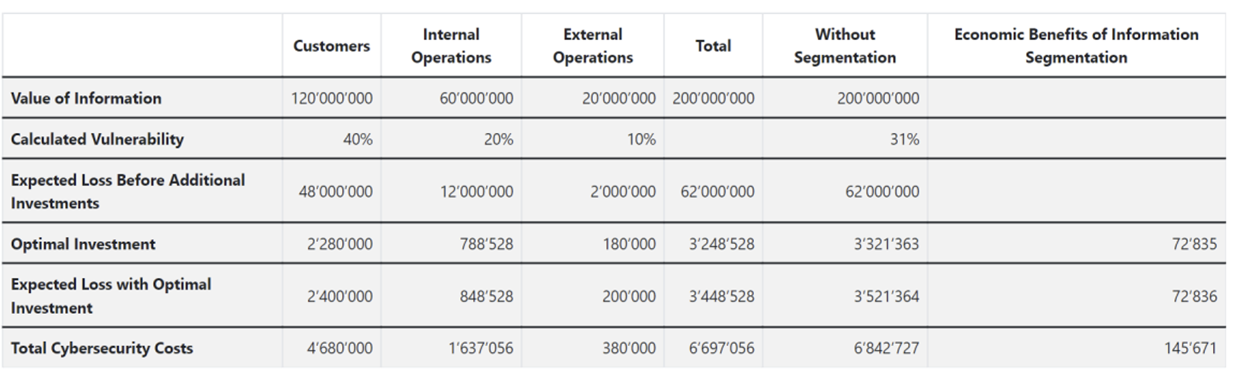
Table1: Example Values of Costs and Benefits Calculated by the SECAdvisor Tool
Thus, solutions like SECAdvisor can benefit SMEs around the globe in better planning and investment decisions in cybersecurity, while they also support the analysis of possible financial losses due to a successful cyberattack. Besides cybersecurity solutions, key investments have to be made to increase cybersecurity staff and promote cybersecurity awareness for their general employees. Also, companies have to ensure that they can detect and mitigate cyberattacks effectively, with a clear cybersecurity strategy tailored for the reality of the company, e.g., targeting personnel culture, size, sector, and budget, while covering all relevant facets of cybersecurity, i.e., detection, mitigation, and recovery plans.
References
[1] Bruno Rodrigues, Muriel Franco, Geetha Parangi, Burkhard Stiller: SEConomy: A Framework for the Economic Assessment of Cybersecurity; 16th Conference on the Economics of Grids, Clouds, Systems, and Services (GECON 2019), Leeds, UK, September 2019, pp 1–13. URL: http://www.gecon.info/articlesgecon2019/no13_paper31.pdf
[2] Muriel Franco, Noah Berni, Eder Scheid, Bruno Rodrigues, Christian Killer, Burkhard Stiller: SaCI: a Blockchain-based Cyber Insurance Approach for the Deployment and Management of a Contract Coverage; 18th International Conference Economics of Grids, Clouds, Systems, and Services (GECON 2021), “Lecture Notes in Computer Science”, Virtually, Europe, Springer, No. 13072, September 2021, pp 79–92. URL: https://files.ifi.uzh.ch/CSG/staff/franco/extern/publications/GECON_2021-SaCI.pdf
[3] Christian Omlin, Muriel Franco: SECAdvisor: a Visual Tool for the Support of Cybersecurity Investments; January 2022, URL: https://gitlab.ifi.uzh.ch/franco/secadvisor
(By Muriel Franco, Bruno Rodrigues, and Burkhard Stiller, (Communication Systems Group CSG, Department of Informatics IfI, University of Zürich UZH)
