Ethereum’s P2P network monitoring and Sybil Attack Prevention
In our previous blog post “Assessing blockchains’ network infrastructure: why it matters for cybersecurity”, we motivated why the monitoring of blockchains’ underlying P2P network is critical to evaluate network properties impacting their resiliency and to detect suspicious nodes that can threaten the proper functioning of the P2P network, for instance by performing a Sybil attack[1].
Our current work investigates Ethereum’s P2P network for which we developed an open source crawler that can make a precize inventory of all the peers constituting Ethereum’s P2P. Thanks to our crawler, we gathered and analyzed two one-month datasets that we also released publicly. Our results show that the Ethereum P2P network exhibits good structural properties like a decent geographical distribution of peers around the world and a moderate churn rate, but also more concerning ones like a high centralization of the nodes in a few Autonomous Systems only (the top 1% of ASes hold 78.6% of Ethereum nodes).
The size of the network has been stable for several months but suddenly rose in February 2022 to double the network size at its peak, without obvious explanation nor pattern that could characterize the newcomers. The spike is clearly visible in Figure 1 or directly on the the website exposing live data.
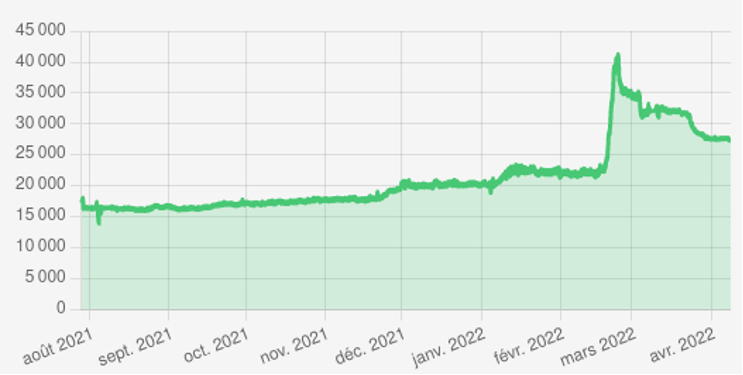
Figure 1: Number of Ethereum’s reachable nodes found in time
The resiliency of a fully distributed P2P network comes from the distribution of the load on independent peers. To evaluate this aspect, we considered three categories of threats that denote a risk that a group of peers is likely controlled by a single entity who could get too much weight in the network: 1) a given /24 subnetwork running many peers, 2) an IP address holding many identities[2], or 3) groups of peers that are statistically too close in the P2P network virtual address space. We found thousands of suspicious peers, mainly falling in the second category (see Figure 2).
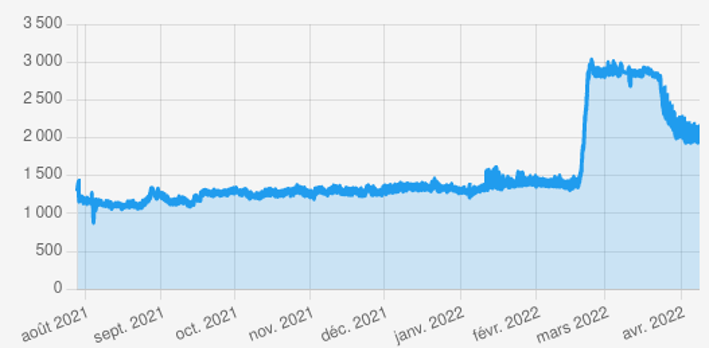
Figure 2: Number of IP addresses holding two or more Ethereum NodeIDs
To prevent possible collusion of peers, we proposed a system (illustrated in Figure 3) to notify when a Sybil attack is at risk and that preventive revocation actions are required. It is based on a smart contract that stores on the Ethereum Blockain the suspicious nodes found by a trusted monitoring system. Then, each peer of the network must verify the reported anomalies on his own by issuing requests on the P2P network and revoke its connections with the suspicious peers he witnesses, ensuring a fully distributed revocation process. In addition to the smart contract, we provided an external tool based on RPC to provide Ethereum clients with these features. Both are open-source and available on this git repository.
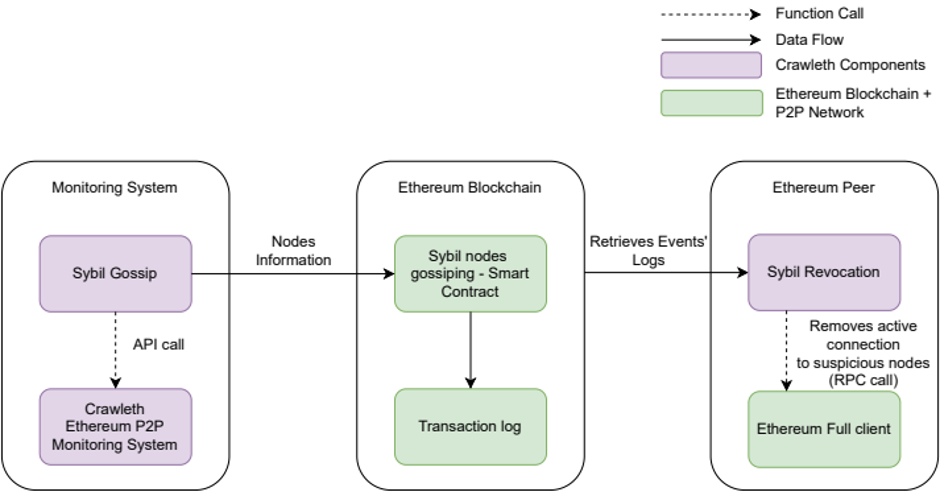
Figure 3: Architecture of our system to monitor and prevent Sybil attacks
In the current state of our work, we can only suspect a group of peers. The next step consists in a deeper investigation of the suspicious peers by issuing application-level messages to them to assess their behavior and possibly characterize attacks.
(By Thibault Cholez, Jean-Philippe Eisenbarth, Olivier Perrin. University of Lorraine)
References
[1] Douceur, J.R.: The sybil attack. In: Revised Papers from the First International Workshop on Peer-to-Peer Systems. p. 251–260. IPTPS ’01, Springer-Verlag, Berlin, Heidelberg (2002)
[2] by identity, we refer to the NodeID which is the generated public key of a node
