Opportunistic Cyber Threats in a Time of Pandemic
The Coronavirus pandemic has spread globally in a matter of weeks, infecting hundreds of thousands while catching the medical community by surprise. While we know where the pandemic originated, we still know very little about cures, treatments, or even a way to immunize patients from it.
However, two things also spread along with the virus: panic and misinformation. In a digital world, these two can be very effective weapons in the hands of cybercriminals, especially when their goals are financially motivated. And make no mistake, everything in the cybercriminal community is financially motivated; from sdata that is stolen in transactions through obscured forums, to ransom demands from cybercriminals who lock you out of your data.
All Attacks Being Equal, Healthcare Took a Beating
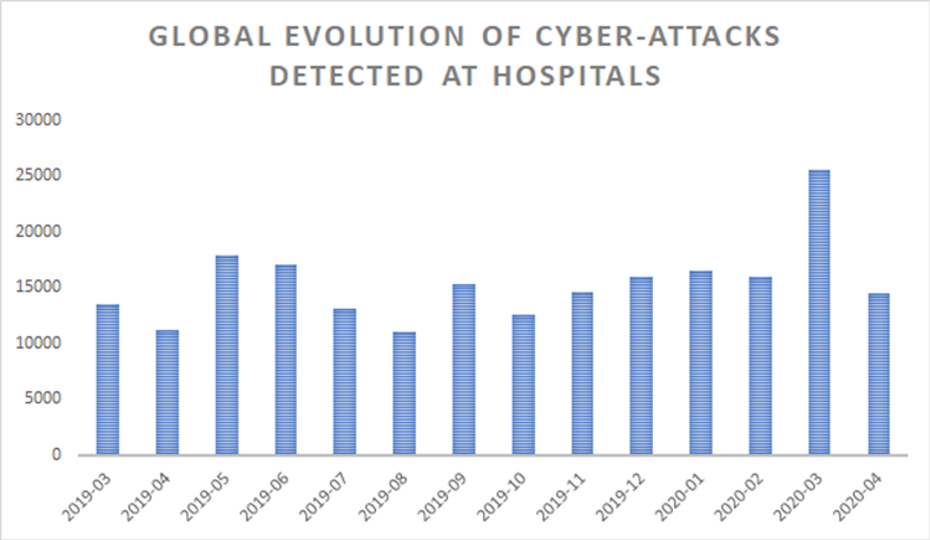
While Bitdefender’s telemetry revealed that the number of reports related to coronavirus-themed malware increased by more than 475% in March from February, all verticals were equally flooded by a wave of spearphishing and malware attacks that promised everything from cures and treatments to medical supplies and healthcare procedures.
Spearphishing is not new. But add fear, misinformation and a general lack of procedures in terms of how to fight the infection, and cybercriminals exploit the global pandemic to their advantage. The messages impersonated reputable organizations, such as the World Health Organization, NATO, and even UNICEF, claiming to have attachments exclusive information and procedures.
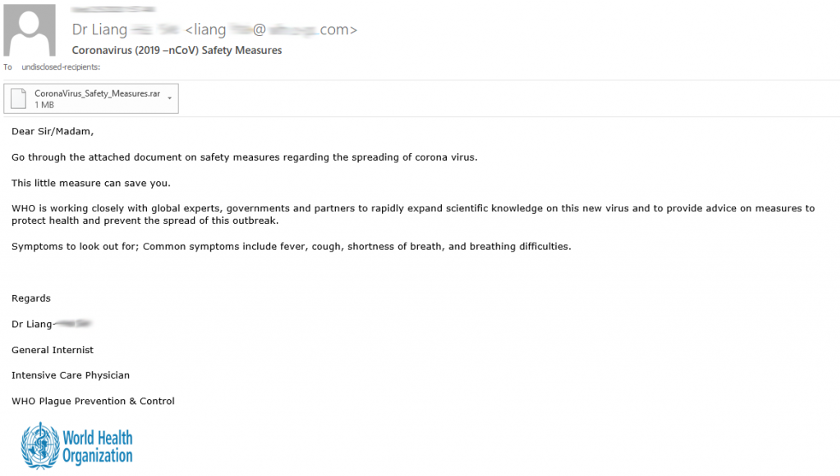
While in other industries these messages might only spur curiosity for the recipient, in healthcare these messages were all the more enticing because medical staff was in dire need of directions and guidance. This is precisely why healthcare was more vulnerable to these messages, and the success rate of these campaigns was higher than in other verticals.
Malware Sophistications Second to Context
Analyzing some malicious payloads delivered by these spearphishing emails reveals that attackers used off-the-shelf information stealers, Trojans, and ransomware, instead of highly sophisticated malware.
However, the careful execution, wording, and sense of legitimacy offered by these emails is something that attackers seem to have focused on more. This shift in tactics by focusing more on the social engineering component and less on malware sophistication is considered the arching conclusion to all the spearphishing campaigns of the past couple of months.
The pandemic was the perfect catalyst for attackers to plan and execute a large number of cyberattacks across all industries, and healthcare is the perfect example of how attackers have amplified their campaigns.
Looking at Times to Come
Cybercriminals seem to have used the pandemic to sharpen their skills at running opportunistic campaigns with themed malware. Although the number of coronavirus-themed malware reports may have slightly fallen during the past couple of months, it’s unlikely that they’ll completely fade away any time soon. As long as people keep getting infected, as long as there’s no cure, and as long as we still fear the virus, cybercriminals will exploit the topic. If anything, should a second wave of infections sweep nations, it’s more than likely cybercriminals will again size the opportunity to use fear as a means to spread malware and themed-threats.
(By Liviu Arsene, Bitdefender)
